On March 4, Broadcom issued VMSA-2025-0004, a VMware security advisory affecting ESXi versions 7.0 and 8.0. Learn more about the three CVEs that make up VMSA-2025-0004 and how to quickly find affected systems using Dynatrace so you can automate remediation efforts.
On March 4, Broadcom issued VMSA-2025-0004, a critical security advisory affecting VMware ESXi versions 7.0 and 8.0. This advisory addresses three distinct vulnerabilities with severity ratings ranging from High to Critical and CVSSv3 scores of 7.1 to 9.3. Organizations running these ESXi versions should prioritize implementing the recommended patches or mitigations to protect their virtualization infrastructure from these significant security threats.
Cybersecurity is a dynamic field with continuously evolving threats. By maintaining up-to-date threat intelligence, organizations can ensure their defense mechanisms remain effective and resilient against emerging vulnerabilities—particularly when addressing known vulnerabilities with established patches. However, identifying threats and planning for their remediation is only part of the equation—implementation is crucial, as strategic knowledge without tactical execution provides no tangible security benefits.
Here’s more about the VMware security advisory and how you can quickly find affected systems using Dynatrace so you can automate remediation efforts.
Understanding the CVEs: VMSA-2025-0004 technical analysis
The VMware security advisory is made up of three vulnerabilities that each present a unique risk:
- CVE-2025-22224
- CVE-2025-22225
- CVE-2025-22226
The only mitigation for all these vulnerabilities is to apply the appropriate ESXi patches described in the How to patch the vulnerabilities section below.
What is CVE-2025-22224?
CVE-2025-22224 describes a time-of-check time-of-use (TOCTOU) vulnerability that leads to an out-of-bounds write, where a program writes data past the end or before the beginning of the intended buffer. With a TOCTOU vulnerability, an attacker can manipulate a system between the time a resource’s state is checked and when it’s used, also known as a race condition. This combination allows a malicious actor with local administrative privileges on a virtual machine to execute code as the virtual machine’s VMX process running on the host.
The CVE-2025-22224 vulnerability scores in the Critical severity range with a maximum CVSSv3 base score of 9.3.
What is CVE-2025-22225?
CVE-2025-22225 refers to an ESXi arbitrary write vulnerability. It allows a malicious actor with privileges within the VMX process to trigger an arbitrary kernel write, which can lead to an escape from the sandbox.
This vulnerability scores in the Important severity range with a maximum CVSSv3 base score of 8.2.
What is CVE-2025-22226?
CVE-2025-22226 is an information disclosure vulnerability in ESXi, Workstation, and Fusion due to an out-of-bounds read in host-guest file system (HGFS−a VMware feature that allows shared folders between the host and guest operating systems for easy file sharing). In this scenario, a malicious actor with admin privileges could exploit this issue to leak memory from the process of interacting with the VMX configuration file.
This vulnerability scores in the Important severity range with a maximum CVSSv3 base score of 7.1.
How to patch the vulnerabilities: CVE-2025-22224, CVE-2025-22225, CVE-2025-22226
You can remediate all three vulnerabilities by applying one patch to ESXi.
The following versions have been released to address issues described in VMSA-2025-0004:
- ESXi 7.0 Update 3s (Build 24585291)
- ESXi 8.0 Update 2d (Build 24585300)
- ESXi 8.0 Update 3d (Build 24585383)
How to quickly detect VMSA-2025-0004 vulnerabilities using Dynatrace VSPM
With Dynatrace VSPM, you can quickly detect the VMSA-2025-0004 vulnerabilities and automate remediation to maintain the security of your workloads.
- Sign in to Dynatrace VSPM.
- Check your Definitions database version:
- Go to Menu > System Settings.
Figure 1. Navigate to System Settings. - From the left Dynatrace menu, go to Updates and confirm that the Definitions database version is at least 6.9.10.1.
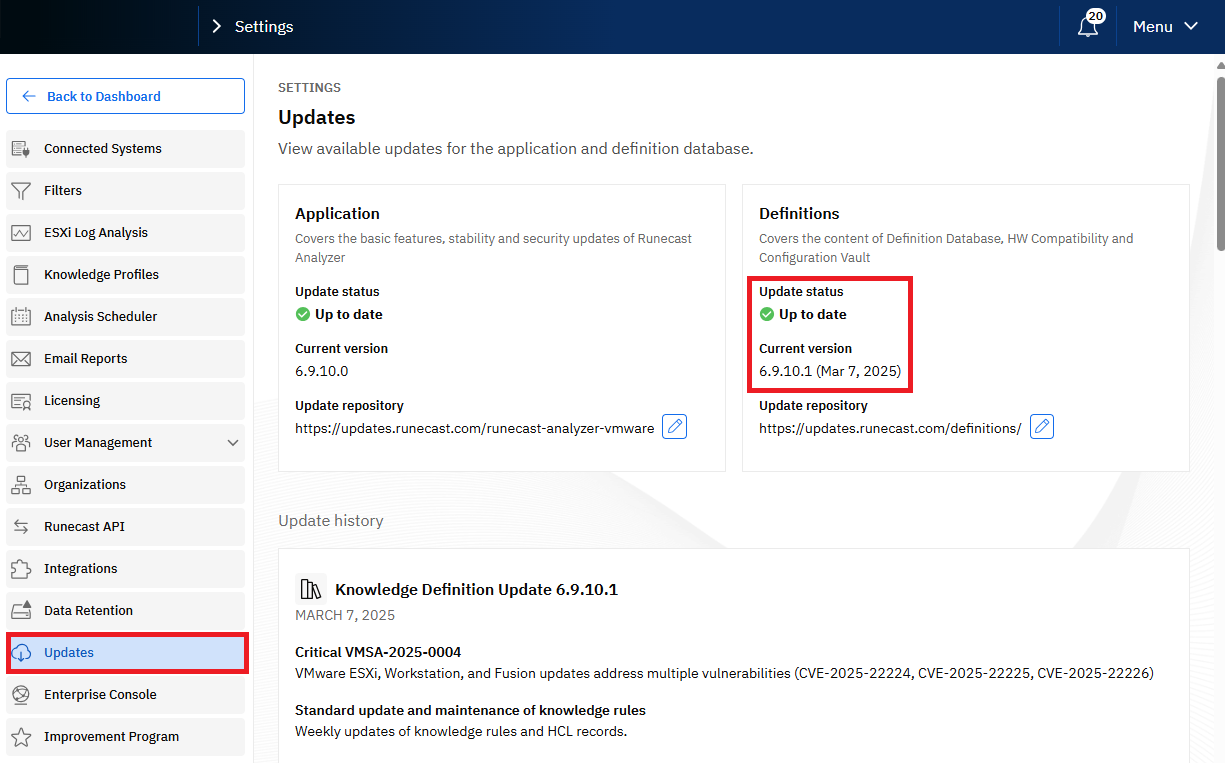
Figure 2. Confirm the Definition database version is at least 6.9.10.1. - If the Definitions database version is lower than 6.9.10.1, perform an update by selecting Update definitions now.
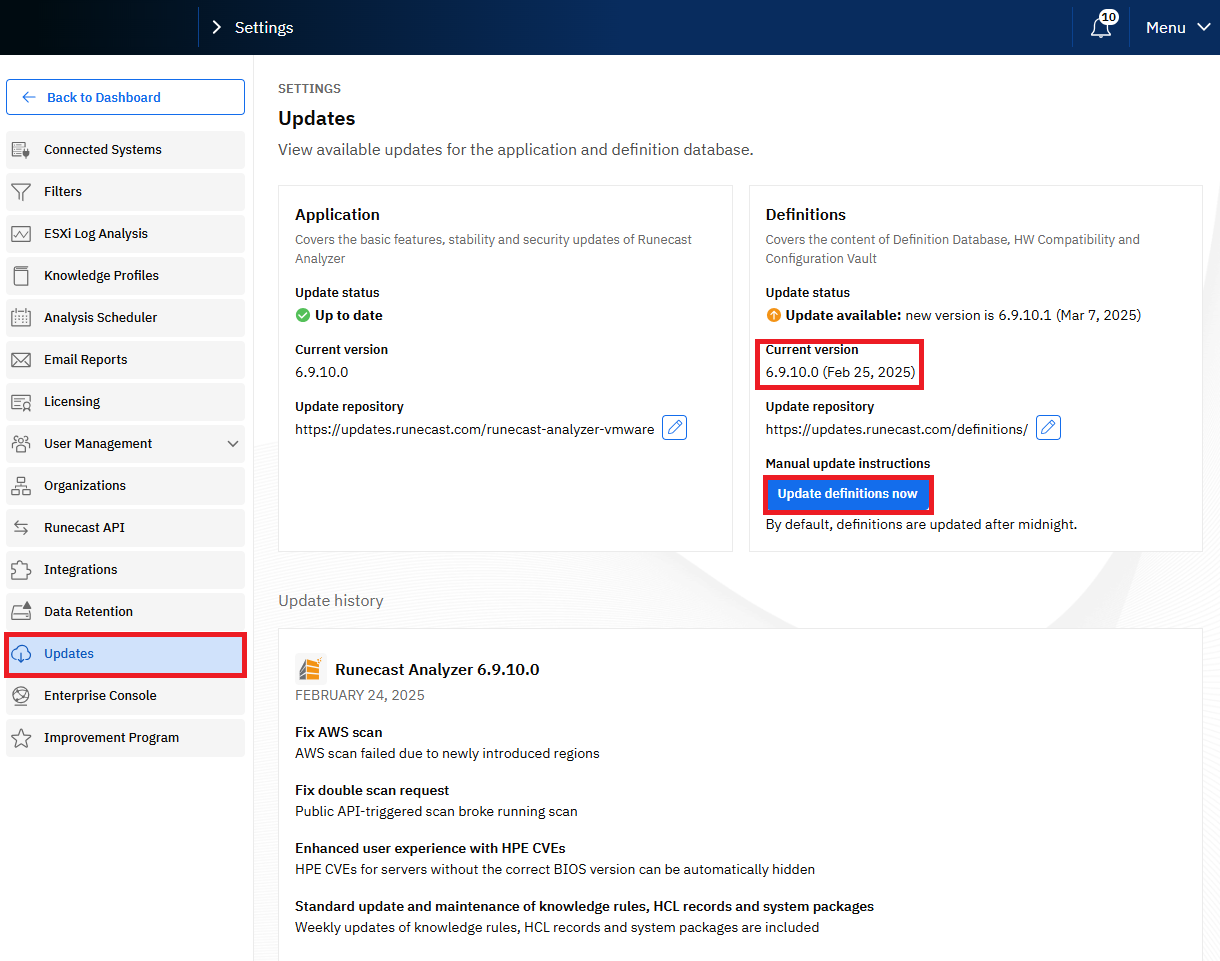
Figure 3. Update the definitions database if needed.
- Go to Menu > System Settings.
- Run analysis of your system(s) by selecting Run analysis.

Figure 4. Run the analysis to find asystems affected by VMSA-2025-0004. - When the analysis is complete, select Vulnerabilities from the left navigation menu.

Figure 5. Navigate to Vulnerabilities. - In the Vulnerabilities screen, you can switch between Focused, Extended and Complete view and use filters to see whether any of your scanned systems are affected by VMSA-2025-0004.

Figure 6. Toggle between views to find systems affected by VMSA-2025-0004. - If any of your systems are affected by VMSA-2025-004, the Response Matrix section provides the patch description, FAQ, and other resources provided by VMware/Broadcom.

Figure 7. Find systems and remediation guidance for systems affected by VMSA-2025-0004
Accelerating vulnerability management and remediation
By implementing Dynatrace VSPM as part of your regular security protocol and adhering to its recommendations, you can achieve several critical security objectives:
- Maintain hardened VMware configurations that effectively minimize your attack surface.
- Streamline security management through automated detection and remediation processes, which significantly reduces the time required for vulnerability management.
- Prioritize known exploits to verify your systems remain protected against critical vulnerabilities.
- Substantially diminish the risk of system compromise from malicious software, including ransomware attacks.
What’s next
To learn more about Dynatrace VSPM, join us for the on-demand webinar, Enhance VMware Security and Compliance with Runecast Analyzer.
Looking to elevate your VMware Security Posture Management? Learn how to achieve proactive issue resolution, continuous compliance and vulnerability management. Request a demo of Dynatrace VSPM.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum