Tracing the early signatures of a vulnerability leading up to it's public disclosure can be crucial for understanding its wider impacts. Here's what we discovered about the Apache Struts CVE-2024-53677 vulnerability as it emerged.
With the increasing frequency of cyber threats, identifying vulnerabilities early is essential. Recently, a critical vulnerability was discovered in Apache Struts, a widely used Java-based web application framework. This vulnerability, published as CVE-2024-53677 on December 11, 2024, affects the file upload mechanism, allowing for path traversal and potential remote code execution. This flaw poses significant risks for enterprises using Struts in their applications.
In our latest research, we analyzed social media, blogs, and other online sources to identify early indicators of such vulnerabilities. Leveraging state-of-the-art language models (LLMs), we uncovered early discussions about Apache Struts CVE-2024-53677 circulating online before its official disclosure. By analyzing this information, we identified key patterns that highlighted the vulnerability’s potential impact ahead of time.
For a comprehensive technical breakdown of this vulnerability, including its exploitation mechanism and affected versions, refer to our blog post, The anatomy of broken Apache Struts 2: A technical deep dive into CVE-2024-53677. This post provides an in-depth analysis, helping organizations understand the vulnerability’s impact and necessary remediation steps.
Our detailed analysis not only illuminates the specifics of CVE-2024-53677 but also offers practical measures to secure your software systems against similar threats. By understanding and addressing these early indicators, you can transform potential vulnerabilities into manageable challenges, ensuring your systems remain secure and resilient.
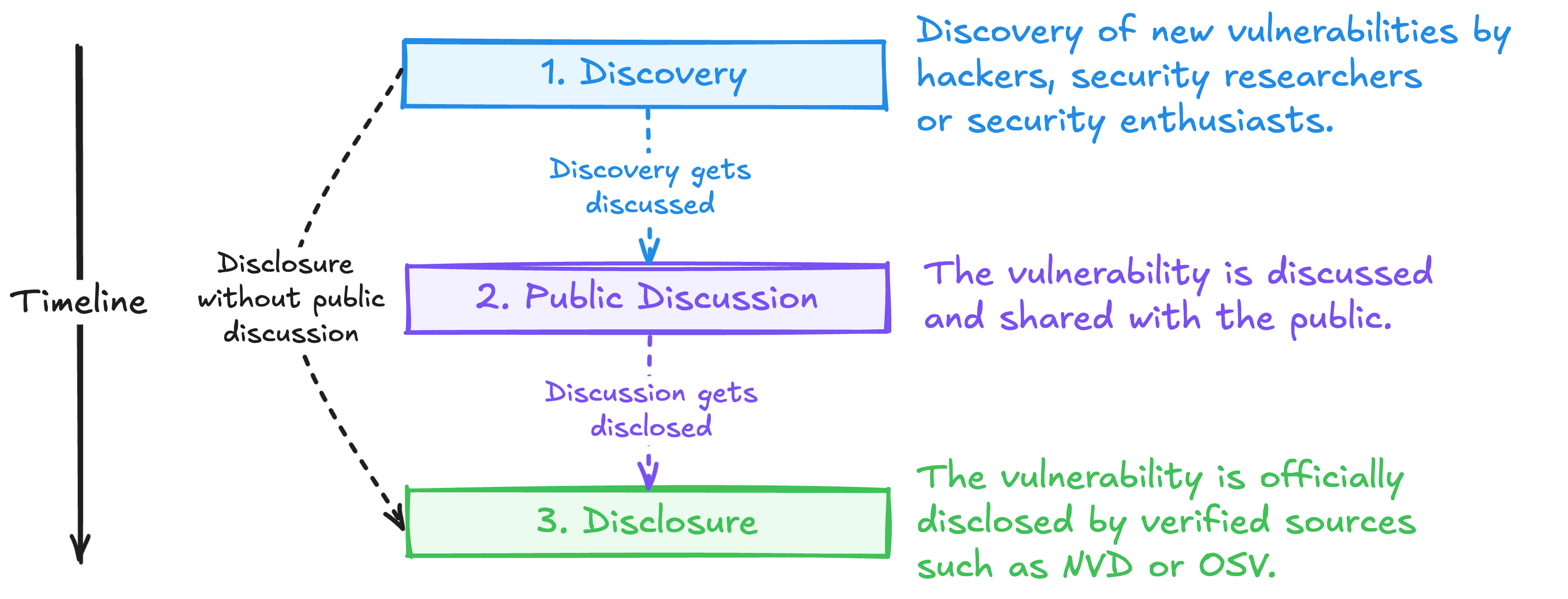
The investigation lifecycle of a vulnerability
The lifecycle of a vulnerability involves several stages, including discovery, discussion, and disclosure. Organizations can better protect their systems and data from exploitation by comprehensively addressing each phase. Below we provide a brief overview of the three stages that we identify.
The Apache Struts CVE-2024-53677 vulnerability
Apache Struts is a popular open-source framework for dynamic web applications with Java. It utilizes a Model-View-Controller (MVC) architecture to separate business logic, page design, and control flow. This recent critical vulnerability in its file upload mechanism carries a CVSS rating of 9.5 out of 10.
This critical flaw allows for a path traversal attack, enabling attackers to upload malicious files and potentially execute arbitrary code on the server. Attackers can leverage this to manipulate parameters to bypass security mechanisms and upload files to arbitrary locations. A proof of concept (PoC) exploit for CVE-2024-53677 published by EQSTLab demonstrates how this vulnerability can be exploited for path traversal and remote code execution.
Timely insights for new vulnerabilities
Investigating new vulnerabilities is crucial for the integrity and security of software systems. To detect any possible effects of the vulnerability before it was published, we cross-referenced data from multiple sources, scraping Jira, Mastodon, GitHub, and various security blogs. Using this method, we identified indications of the potential vulnerability in the Apache Struts package long before the official publication date.
By analyzing commits, pull requests, and issue reports on GitHub and Jira, we identified further indicators that point to potential vulnerabilities. Additionally, we searched and analyzed multiple security blogs and forums for expert insights and further detailed analysis of vulnerabilities. To handle the challenging and time-consuming process of collecting, processing, and analyzing this information, we automated it with an LLM-based multi-agent framework. This allowed us to identify relevant information and obtain a detailed understanding of CVE-2024-53677.
Uncovering the Apache Struts vulnerability
Our investigation into CVE-2024-53677 began with a deep dive into various online discussions and issue trackers. We uncovered a trail of breadcrumbs leading back to April 2024 on the Apache Struts Jira issues page, well before the official publication date in December 2024. This early chatter highlights how discussions around vulnerabilities can surface in informal channels before being formally recognized by official sources.
Evidence from Apache Struts Jira issues
Our first clues came from the Apache Struts Jira issues page, where we found several discussions that, while not explicitly mentioning CVE-2024-53677, highlighted significant concerns about the file upload mechanism, more specifically, the associated interceptor class responsible for handling such uploads. This mechanism is crucial because it potentially allows path traversal and malicious file uploads. Furthermore, understanding the role of the file upload mechanism is essential to determine the severity of CVE-2024-53677.
- Issue WW-5413 (released on April 13, 2024): This issue discusses a vulnerability in the file upload mechanism that could lead to unauthorized access and data leakage. The comments pointed out the risk of unauthorized access due to flaws in the file upload mechanism.
- Issue WW-5474 (released on October 18, 2024): This issue discusses problems with the file upload mechanism, specifically mentioning the
struts.multipart.maxFilesparameter not working as expected. This directly relates to the path traversal vulnerability that allows attackers to upload files to arbitrary locations.
Evidence from security blogs and forums
With the information from the Apache Struts Jira issues page, we had already established evidence of a potential vulnerability in the file upload mechanism. Next, we analyzed related discussions about the vulnerability using information from security blogs and discussion forums on Mastodon. Using our LLM-based agent and the information from Jira and blogs discussing the vulnerability, we also identified the following Mastodon toot as related to CVE-2024-53677:
- Apache Struts remote code execution blog (published on The Register on December 17, 2024): The blog post mentions that CVE-2024-53677 is potentially associated with the already known vulnerability CVE-2023-50164.
- Remote code execution vulnerability in Apache Struts (posted on Mastodon on December 12, 2023): The toot discusses an inadequate validation in the
FileUploadInterceptorclass, referencing CVE-2023-50164. This involved path traversal and remote code execution in Apache Struts 2. Analyzing this issue, we were able to draw parallels to CVE-2024-53677.
The above toots thus gave us indications about the potentially affected part of the vulnerability, which our security analysts were able to verify. Following our approach, we could uncover a connection between CVE-2024-53677 and CVE-2023-50164.
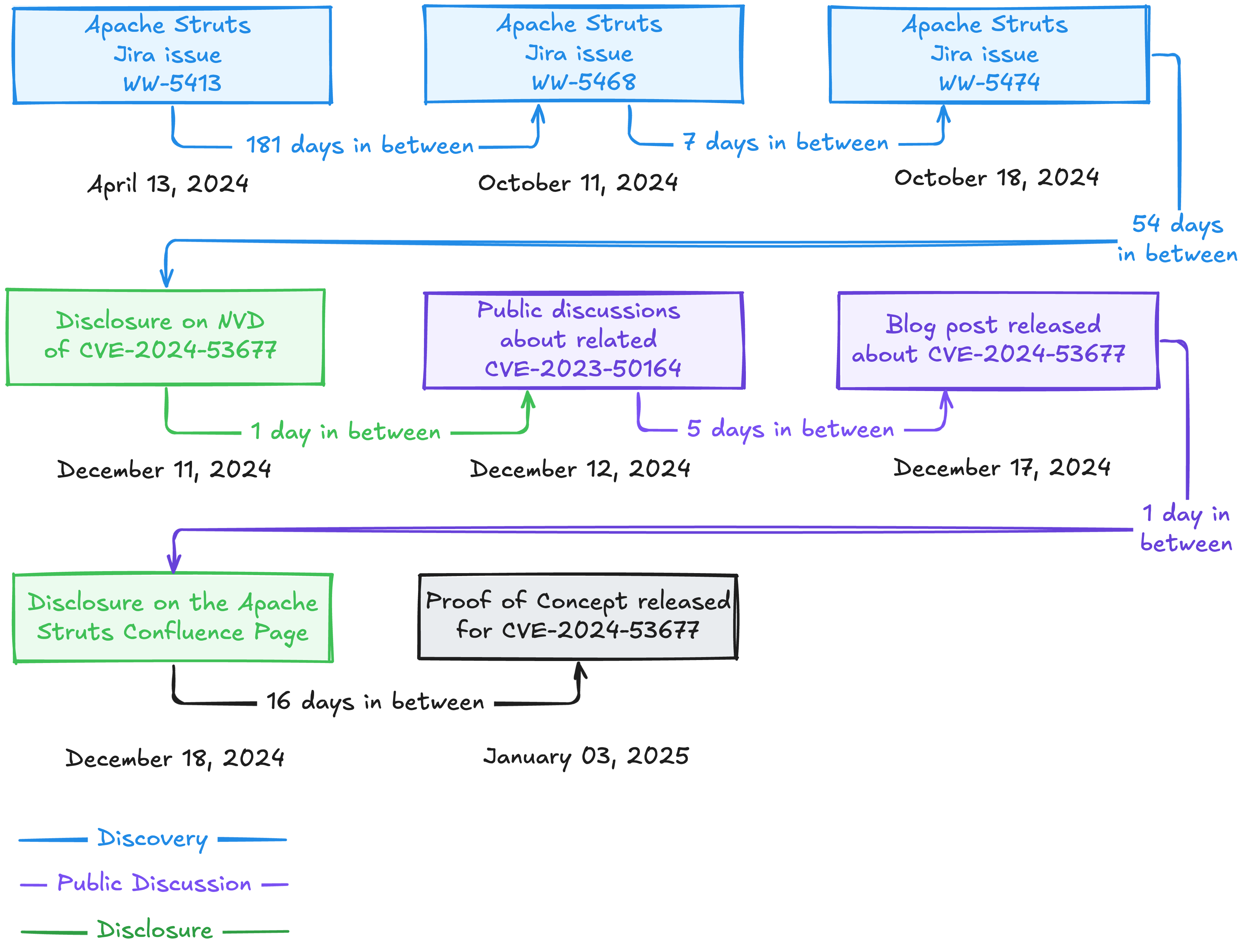
Thus, combining early warnings from Jira issues, information from security blog posts, and discussions in security chats (for example, Mastodon), we discovered crucial insights and information about CVE-2024-53677 that existed before NVD or OSV disclosed detailed vulnerability information (such as vulnerable class or function information).
Why wasn’t this vulnerability fixed sooner?
Despite early warnings from the Jira issues and discussions, several technical challenges delayed addressing CVE-2024-53677.
- Complexity of the file upload mechanism: The file upload mechanism in Apache Struts is inherently complex, involving multiple parameters and configurations, making it difficult to identify and address all potential vulnerabilities promptly. For instance,
strusts.multipart.MaxFilesspecifies the number of files able to be uploaded in a single request. In issue WW-5474, it was noted that this parameter was not functioning as expected, leading to potential security issues. Attackers could exploit this flaw by uploading more files than intended leading to a Denial-of-Service (DoS) attack. - Focus on compatibility: Ensuring compatibility with existing features took precedence over addressing security flaws. This can be seen in issue WW-5468, which highlights compatibility issues with the Model-Driven interface and the
@StrutsParameter. These issues are mainly related to the design to protect against arbitrary getters and setters in theActionclass. Similarly, issue WW-5413 discusses that fixing the issue might break functionality, which provoked them to discuss a later release.
What’s next?
Our investigation into CVE-2024-53677 underscores the importance of early investigation of new vulnerabilities and the need to monitor multiple sources for early signs of potential threats. With our approach, we could map the latest Struts vulnerability to information about earlier disclosed vulnerabilities in the Apache Struts project, create deeper insights about the cause of the vulnerability, and recreate a timeline of how the vulnerability evolved.
Dynatrace third-party vulnerability insights provide valuable information to help our customers mitigate threats. By continuously extending our coverage, we ensure optimal protection, emphasizing the importance of staying ahead of potential threats to maintain software security and integrity. See our documentation for more details about detecting and managing third-party vulnerabilities with Dynatrace and to learn more about Dynatrace Runtime Vulnerability Analytics.



Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum