Dynatrace has introduced a convenient and secure way of integrating Dynatrace synthetic monitors with external secret vaults such as HashiCorp Vault and Azure Key Vault. With this new feature, Dynatrace synthetic monitors can monitor websites and API endpoints protected with credentials stored in these external vaults without requiring additional effort from the teams responsible for managing the monitors and credentials.
Strict rules and high volume make for difficult management of secrets
Our customers use Dynatrace Synthetic Monitoring for 24/7 monitoring of their websites, web applications, and API endpoints. These systems are protected by various authorization mechanisms. The problem in modern, complex environments with very strict security rules is that the sheer volume of secrets is not only difficult to manage but is also growing rapidly. To add another layer of complexity, these secrets need to be rotated frequently and regularly to comply with security policies. One of the reasons that companies have opted to use external vault solutions (such as HashiCorp Vault, Azure Key Vault, CyberArk Vault, and others) is to make management of authorization secrets easier.
In a typical setup, the team that maintains synthetic monitors and furnishes them with application credentials is different from the team managing and rotating company secrets in an external vault system. This scenario can present challenges as rotating passwords twice can be redundant and pose a potential security risk. To address such concerns regarding credential rotation and security, we introduced a mechanism for automatically synchronizing credentials stored within Dynatrace with those stored in external vaults.
Auto-synchronized credentials from external vaults
To make synthetic monitoring more effective, we already introduced the Dynatrace credential vault for storing passwords, tokens, and certificates needed by monitors to access API endpoints and websites. Now, with automatic synchronization of credentials, you can easily and securely integrate Dynatrace synthetic monitors with external secret vaults. All you need to do is create a new entry within the Dynatrace credential vault, mark it as synchronized, and provide the necessary details to authorize access to an external vault and path to a particular secret stored there—Dynatrace takes care of the rest!
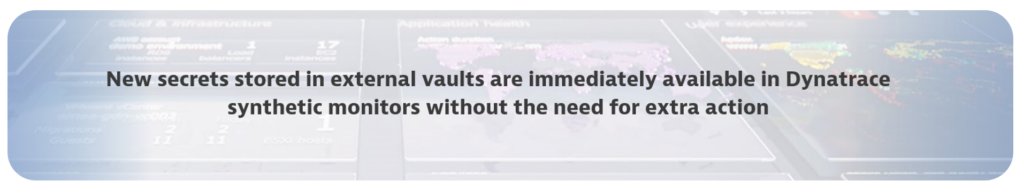
Dynatrace automatically creates a synthetic HTTP monitor whose sole purpose is to synchronize the new entry within Dynatrace vault with data stored in the external vault. This synchronization is automatic with no additional actions required on the part of the teams managing your Dynatrace synthetic monitors.
How it works
There’s a small albeit important new element when creating new credentials within the Dynatrace credential vault—a toggle for enabling synchronization with an external vault.
After turning the toggle on, you need to select the type of external vault that contains the source credentials. Next, you’ll need to provide details regarding the exact location, such as the URL of the external vault of the secrets you want to synchronize as well as the preferred method for authenticating within the external vault. At the time of this publication, HashiCorp Vault and Azure Key Vault are the supported external vault types with AppRole-based or certificate authentication for HashiCorp and certificate authentication for Azure Key Vault.
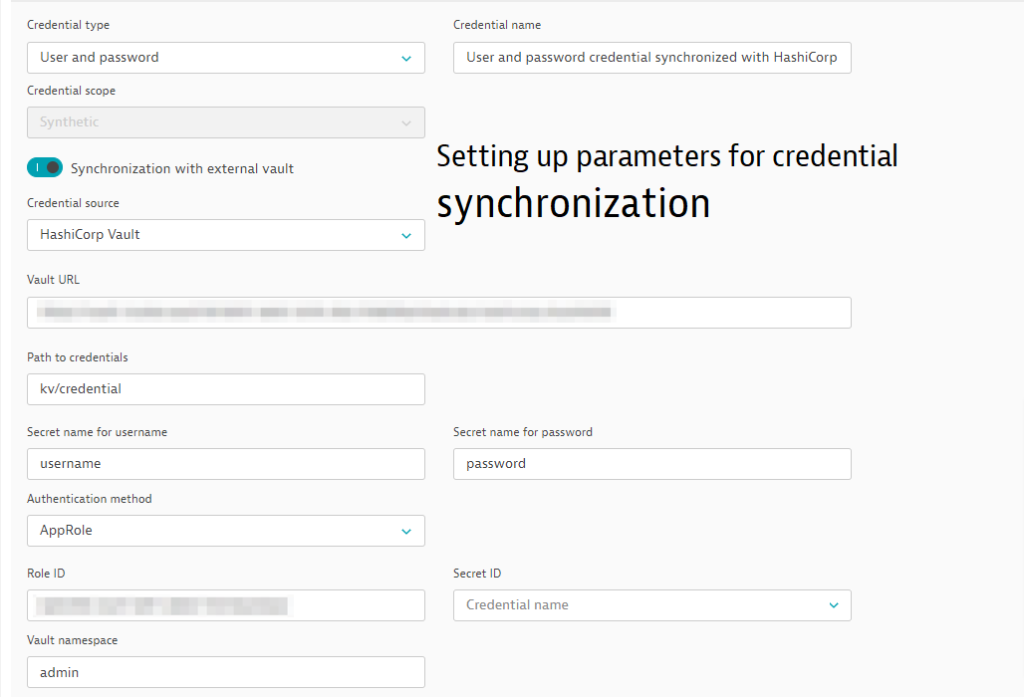
You can find a detailed description of how to set up a credential for external synchronization in Dynatrace Documentation. Note that you never need to provide sensitive information as plain text; it’s quite the opposite—any such information would need to be stored in the Dynatrace credential vault in advance and used directly from here.
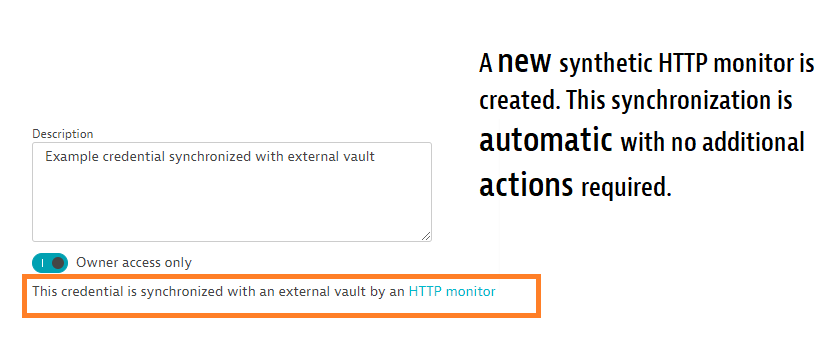
After you’ve set up and saved the credential to be synchronized, a new synthetic HTTP monitor is automatically created with the goal of executing the requests necessary for performing secret synchronization. Its configuration is based on information provided earlier. You can analyze the execution details of an automatically created synchronization monitor in the same way as you would any other HTTP monitor. However, please note one important difference—to ensure the security of secrets, the details of headers and payloads are not stored to avoid exposing the secrets in execution details.
By default, synchronization monitors are assigned to a single location and run once an hour, but those values may be adjusted as needed. From each synchronized entry within the Dynatrace credential vault, there’s a link to the HTTP monitor performing synchronization.
Overwriting a credential that’s synchronized with an external vault achieves a slightly different end than in the case of standard credentials. The goal here is not to provide a new password or username value, but, rather, to adjust parameters necessary to access data from the external vault.
Of all the ways we could have implemented credential synchronization, we opted for synthetic monitors for one special reason—it makes it possible for you to adjust their definitions easily in order to build your own support for a different authorization method or experiment with different vaults. If keeping a copy of your credential within the Dynatrace credential vault is forbidden, you might consider obtaining the secret directly within the monitors testing the business logic of your application.
What’s next
Synchronization with external vaults is not our only big improvement for Dynatrace Synthetic Monitoring—expect more to come soon. In particular, keep an eye out for:
- On-demand triggering of synthetic monitor executions.
- Deployment of containerized private Synthetic locations within Kubernetes clusters.
Get proactive with Synthetic Monitoring
External credential synchronization is available with Dynatrace version 1.239. For private locations, ActiveGate 1.237+ is required. With these conditions met, you may start configuring synchronization of your secrets for use within your synthetic monitors.
Please don’t forget to share your comments with us. You can find me on the Dynatrace Community, or you can leave your comments in the Product Ideas channel focused on external credential vaults. Your feedback will be factored into decisions around which other external vaults should be supported (CyberArk is top candidate right now) or which other authentication mechanisms are in demand.
New to Dynatrace? Sign up for a free trial.




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum