In the following RSA 2022 guide, we explore the benefits of DevSecOps transformation through runtime vulnerability management and application security in multicloud environments. These resources examine how teams can transform their approach to application security and protect their cloud-native environments from runtime vulnerabilities.
How to build application security into DevSecOps transformation
As organizations undergo DevSecOps transformation and their IT complexity proliferates, security teams need their vulnerability management approach to be seamless.
Because of this IT complexity, security teams are on the front lines of organizational success and resilience.
In addition, as businesses of all kinds adopt cloud-native and open source technologies, their environments become more flexible. However, these technologies can add to the complexity. Cloud environment toolkits —microservices, Kubernetes, and serverless platforms — deliver business agility, but also create complexity for which many security solutions weren’t designed.
As a result, while cloud architecture has enabled organizations to develop applications iteratively, it also increased exposure to vulnerabilities. Because of their flexibility, dynamic, ephemeral environments are more difficult to monitor in real time than traditional on-premises infrastructure. Therefore, application vulnerabilities can proliferate quickly and threaten sensitive employee or customer data.
Above all, companies modernize and adopt a multicloud strategy to innovate, scale, and increase efficiency. However, using traditional monitoring approaches with these technologies only compounds these vulnerability blind spots. Because data is more distributed and teams collaborate globally with cloud-based applications, IT teams struggle to keep up with the vulnerabilities that threaten these systems.
At RSA 2022, the theme is Transform. Accordingly, as organizations undergo DevSecOps transformation to innovate, reduce costs, and enable dispersed teams, they need to safeguard IT systems from performance problems and security breaches.
Automation for application security
Over the past several years, the volume of malicious attacks has eclipsed the ability to effectively monitor IT environments for vulnerabilities with human effort alone.
As a result, organizations can’t play catchup after a DevSecOps transformation, as vulnerabilities proliferate and morph in an environment. Similarly, teams can’t rely only on manual work to identify and resolve an increasing number of vulnerabilities. Instead, they need to enlist software intelligence to monitor their systems end to end to identify and prioritize remediation efforts.
Explicitly, learn more about how intelligence-enabled observability and application security help DevSecOps teams work smarter, not harder.
 |
Software intelligence as code enables tailored observability, AIOps, and application security at scale – blog
See how Dynatrace enables organizations to apply observability, AIOps, and application security as code, thus helping to reduce app onboarding time. |
 |
AIOps capabilities drive intelligent cloud observability – blog
Multicloud and hybrid cloud environments offer many benefits. But they also introduce overwhelming complexity for organizations. See how causation-based AIOps is a game-changer. |
 |
AIOps strategy central to proactive multicloud management – blog
Cloud complexity is a major challenge for IT teams. So, find out how a sound AIOps strategy is crucial to keeping this complexity in check. |
In addition, check out the Dynatrace Application Security module.
Monitoring multicloud environments and identifying security vulnerabilities
Notably, the need to innovate faster and shift to cloud-native application architectures is driving more than complexity. Above all, it’s creating vulnerability blind spots. However, with AI at the core of a modern observability platform, organizations can identify these blind spots in real time. Additionally, that can reduce manual effort to identify vulnerabilities and lay the foundation for less time-consuming and more automated issue remediation.
 |
Runtime vulnerability management is still a vexing challenge for organizations – blog
Organizations are releasing code faster to keep up with today’s competitive landscape. But rapid code cycles also introduce runtime vulnerability management threats. |
 |
Why vulnerability management enhances your cloud application security strategy – blog
Moving to cloud-based services makes app security critical. Therefore, it’s crucial to learn how vulnerability management can better secure apps in multicloud environments. |
 |
Modern approaches to observability and monitoring for multicloud environments – blog
AND SO Multicloud environments need a modern approach to observability with continuous automation and AI at its core. As a result, it’s important to know how to transform your data. |
 |
Dynatrace accelerates the convergence of observability and security with the acquisition of SpectX – blog
THUS, Modern cloud environments are overwhelming organizations with massive data volumes. See how SpectX further enables Dynatrace to address these challenges. |
 |
RSA 2022: Why modern observability forwards application security objectives – blog
Modern observability platforms have become critical to ‘shifting left,’ and finding code issues in development as well as to ‘shifting right,’ and identifying vulnerabilities in live applications. |
Runtime vulnerability management
Today, organizations can move faster and innovate more easily through software development. But some of this agility involves enlisting third-party code libraries that can also contain vulnerabilities. If undetected, these threats can wreak havoc when applications are live and in production. For example, the recent Log4Shell and Spring4Shell vulnerabilities.
As a result, organizations need visibility into production vulnerabilities in real time. According to recent data, the average time to identify and patch a vulnerability can be more than 200 days. How can organizations get ahead of runtime vulnerabilities before they affect sensitive consumer or employee data?
 |
What is Log4Shell? The Log4j vulnerability explained (and what to do about it) – blog
Log4Shell is a potential threat to millions of applications and devices globally. But what is Log4Shell exactly, and how can organizations combat it? |
 |
How Dynatrace uses Dynatrace to combat the Log4j vulnerability (Log4Shell) – blog
Discover how Dynatrace tackled the Log4j vulnerability, Log4Shell, in real time not only for its customers but for Dynatrace itself. |
 |
Identify and minimize production risk of Log4Shell – blog
Combatting Log4Shell requires a plan around public internet exposure, sensitive data access, and application lists. Therefore, it’s vital to learn how to minimize your risk. |
 |
Log4Shell highlights the need for secure digital transformation – blog
CONSEQUENTLY, Modern observability and vulnerability management gave Avisi the secure digital transformation strategy they needed to conquer Log4Shell. |
 |
Spring4Shell: Detect and mitigate new zero-day vulnerabilities in the Java Spring Framework – blog
Just as organizations learned how to combat Log4Shell, then Spring4Shell sprang into action. Discover how to detect and mitigate this zero-day vulnerability. |
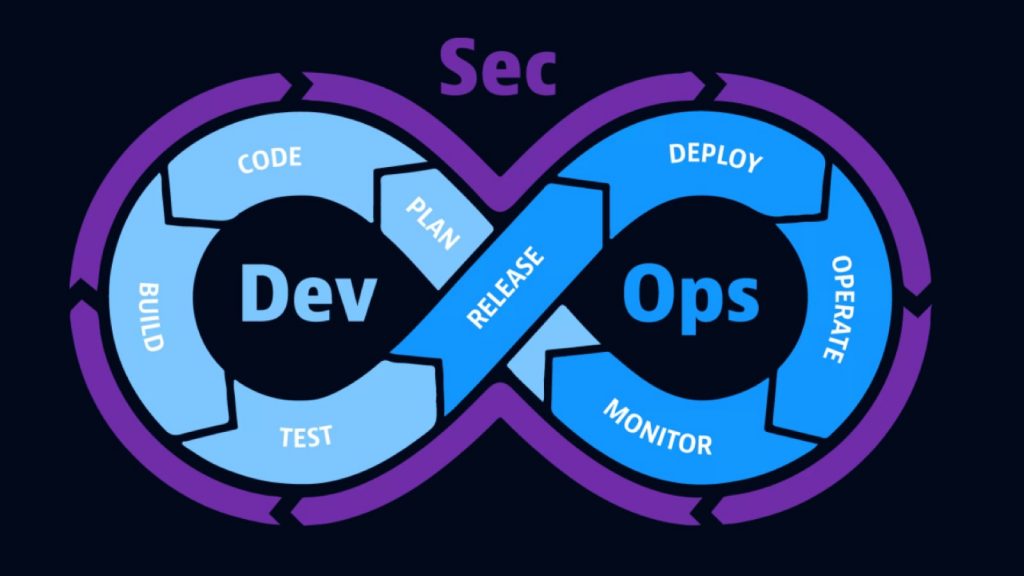
DevSecOps transformation for cloud-native environments
In short, organizations can’t get mired in operational silos and inefficient work processes. So, the DevSecOps methodology brings together development, security, and operations teams to release better software faster and to detect and respond to software flaws in production faster and with greater efficiency.
But development and operations teams can treat security as an afterthought. Indeed, according to Dynatrace research, 63% of chief information security officers say developers don’t always have time to scan for vulnerabilities in their code and apply a fix before the application is pushed to production. Particularly, learn more about how DevSecOps transformation helps organizations develop more secure software faster.
 |
Cloud application security: The next generation – eBook
Organizations’ attack surfaces continue to grow, so it’s more important than ever to incorporate security into development and operations. Learn more. |
 |
Automated DevSecOps release validation ensures security by default – blog
Cloud-native environments rely on microservices, so an automated approach to security enforcement is key. See how the transformation to DevSecOps can help teams keep pace especially without sacrificing security. |
 |
What is DevSecOps? And what you need to do it well – blog
DevSecOps connects three different disciplines altogether: development, security, and operations. Find out what it is, its pros and cons, and more. |
 |
DevSecOps — Development, security and operations – resource
Get an in-depth look at Dynatrace’s approach to DevSecOps. Especially, how your organization can speed risk analysis, remediation, and collaboration with Davis. |
 |
Doing DevSecOps Right – research report
Research from Dynatrace reveals what 700 chief information security officers (CISOs) think about DevSecOps transformation from traditional security tools to modern application security. |





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum