Dynatrace integrates with Harbor to break the silos between DevSecOps teams by unifying security findings along the Software Development Lifecycle (SDLC) and enriching them with runtime context. Dynatrace allows you to ingest, visualize, prioritize, and automate security findings, helping to reduce noise from alerts and provide focused remediation on the issues that matter most to your critical production environments.
Manage vulnerabilities in a fragmented world
In today’s complex digital landscape, managing vulnerabilities effectively is crucial for maintaining robust security. However, the challenge often lies in the fragmentation of vulnerability data across different systems and tools.
Dynatrace provides deep insights into application runtime, offering a detailed view of how applications perform and the runtime impact of potential vulnerabilities. Meanwhile, Harbor continuously scans container images stored as artifacts in a registry for vulnerabilities.
DevSecOps teams that must address vulnerability findings are typically overwhelmed by the number of issues generated from assessments of the various artifacts. But should your teams care about all the findings? A good example is a critical severity vulnerability discovered in a build-time artifact, such as a container image that isn’t deployed and doesn’t impact your runtime. Your DevSecOps teams shouldn’t be distracted by such findings and should focus on vulnerabilities in your production application that are exposed to the internet and present an actual risk.
The Dynatrace solution
Dynatrace addresses these issues by providing unified security event ingest and analysis for security findings across tools and products. Ingested events are stored in the semantic dictionary, which allows you to efficiently visualize, analyze, and automate the orchestration of security findings in a unified and product-independent way.
In addition, with runtime entity contextualization, security findings can be mapped to monitored entities. This runtime context can be used to better prioritize findings based on runtime properties, such as focusing only on vulnerabilities that affect production applications.
Integration with Harbor
Dynatrace delivers Harbor integration as an extension that allows granular control over the data flow between Harbor and the Dynatrace platform.
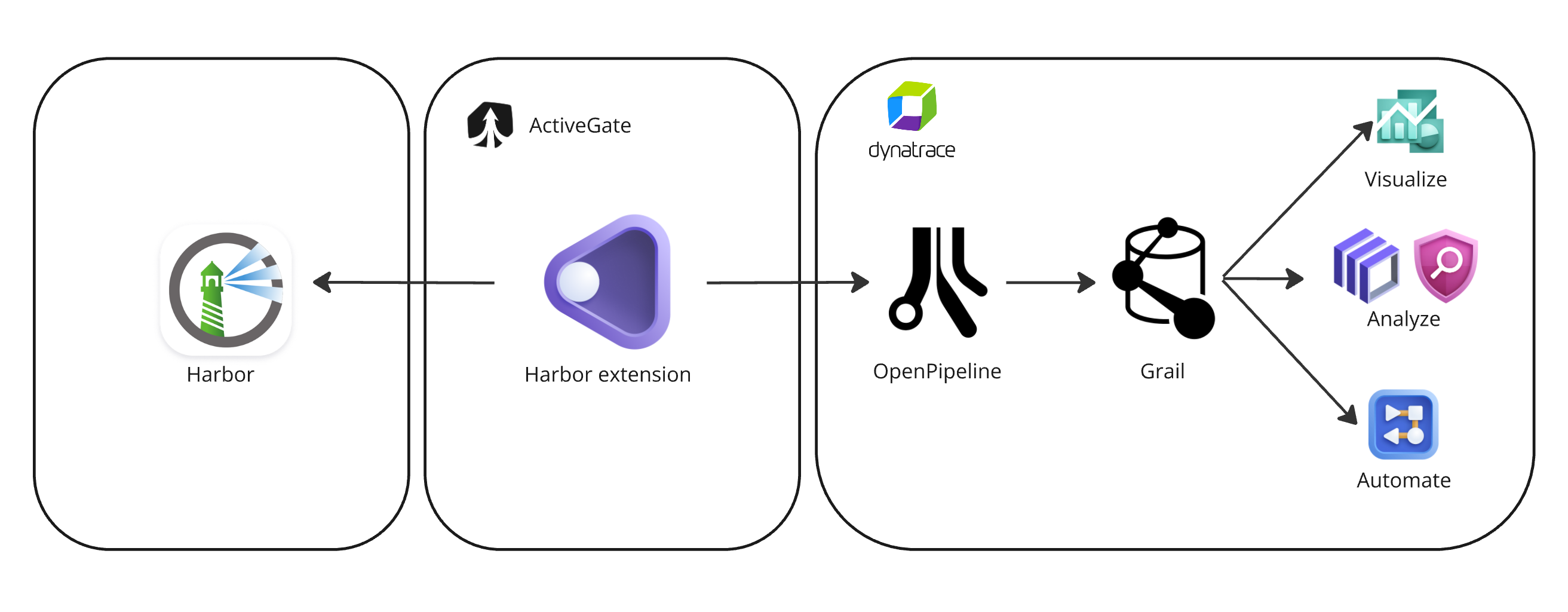
- Harbor vulnerability findings and audit logs are fetched periodically and pushed to Dynatrace via a dedicated security event ingest endpoint.
- Events are processed, mapped to the Dynatrace Semantic Dictionary in OpenPipeline™, and stored in Grail™.
- With sample dashboards and workflows, you can start prioritizing and automating the orchestration of your Harbor vulnerabilities.
As part of this integration, we provide ready-made documents that can serve as a starting point for your data analysis and automation use cases.
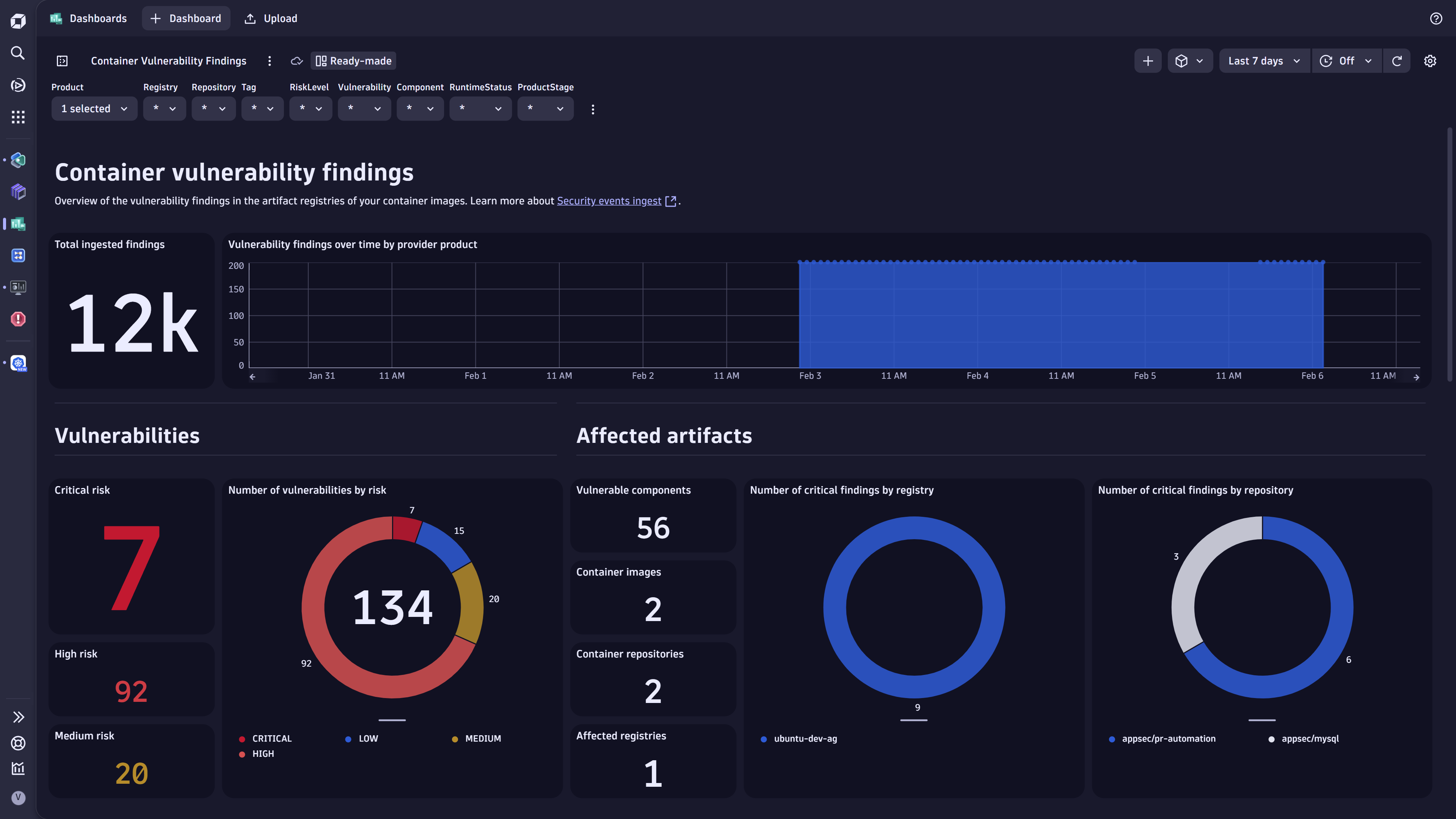
Use case: Visualize and analyze security findings
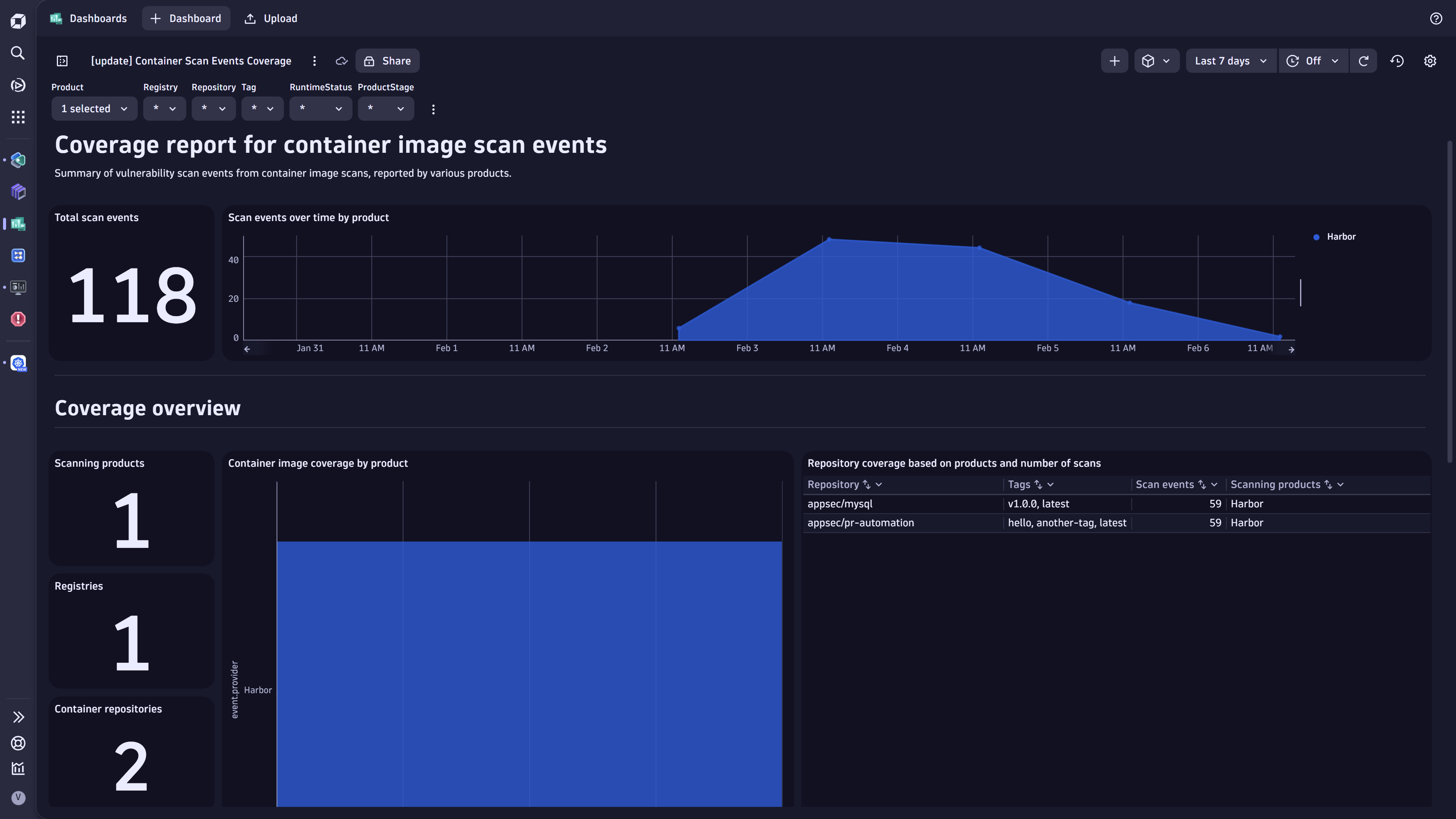
Use case: Discover coverage gaps in security scans
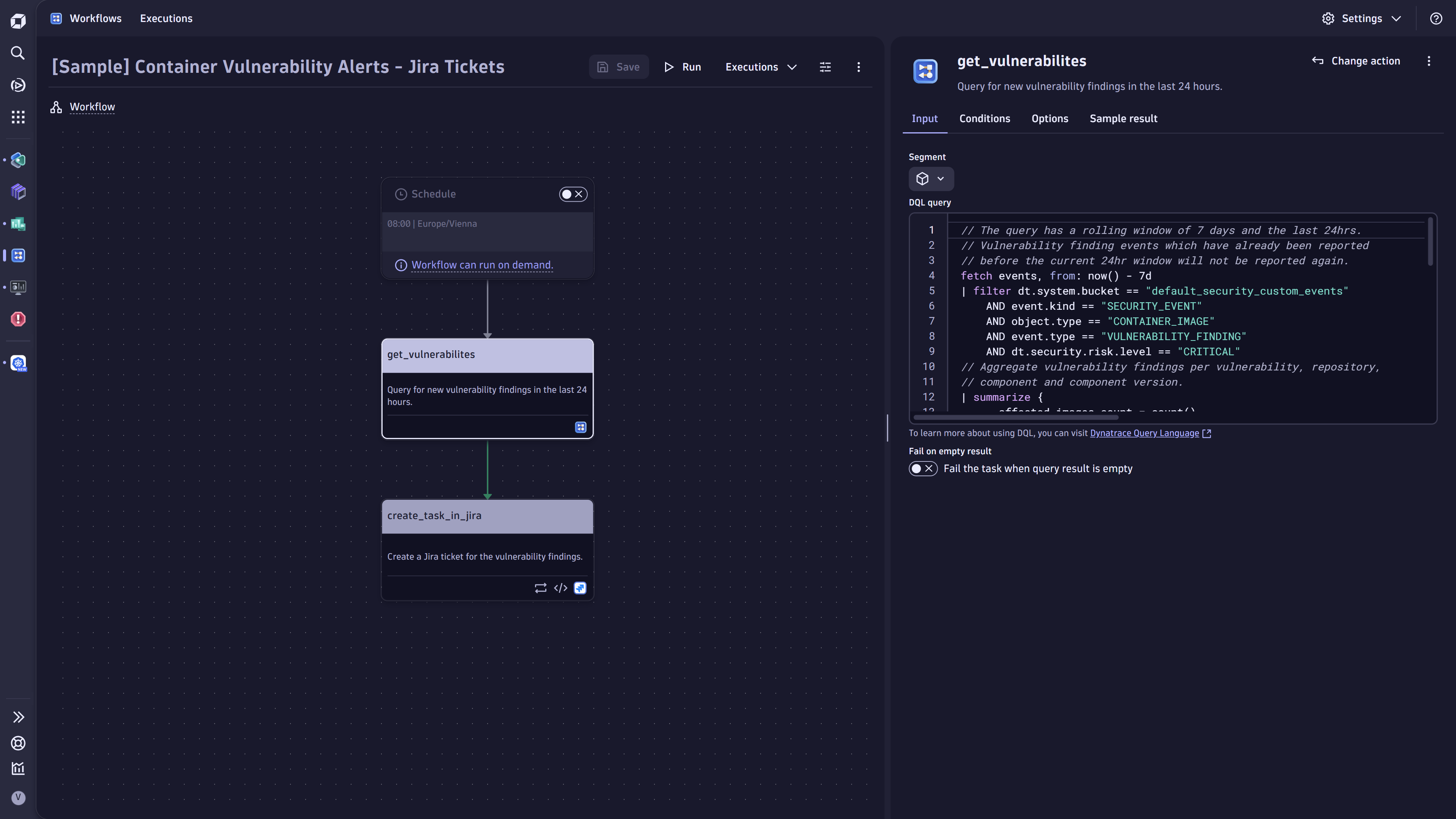
Use case: Automate and orchestrate security findings
Get started
The Dynatrace integration with Harbor gives you control over your security findings and helps your DevSecOps teams focus their remediation efforts.
For more details about the prerequisites and setup instructions, see Dynatrace Documentation, Ingest Harbor vulnerability findings, scans, and audit logs.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum