As organizations transition to the cloud and adopt DevSecOps practices, they can move more quickly and flexibly. They can develop software applications rapidly and gain access to extensible cloud resources without having to sink costs into IT plumbing or managing this infrastructure themselves.
But with this speed, agility, and innovation come new challenges.
Risks include performance problems and outages in cloud-native environments, application security vulnerabilities and poor digital experience for customers and other users. Open source code, for example, has generated new threat vectors for attackers to exploit. A case in point is Log4Shell, which emerged in late 2021 and exposed open source libraries to exploitation. Considering open source software (OSS) libraries now account for more than 70% of most applications’ code base, this threat is not going anywhere anytime soon.
To combat these challenges, organizations need an IT culture that addresses security resilience from the outset—also known as security by design—which, in turn, supports business resilience. This approach, however, requires more extensive collaboration between developers, security teams and IT operations teams.
Not surprisingly, the theme of Infosec Europe 2022 Conference is “Stronger together,” putting an emphasis on IT collaboration. The conference’s theme recognizes that IT collaboration, DevSecOps culture, and business resilience are mutually reinforcing the role of DevSecOps teams in addressing application security threats, system downtime, and digital user experience issues.
This guide explores the impact of identifying vulnerabilities in development and in runtime. That means “shifting left” to identify bugs in development and “shifting right” to identify threats that compromise live applications. By improving their DevSecOps practices and capabilities, teams can increase their security resilience.
Resilience in a world of chaotic cyberattacks
As large-scale vulnerabilities such as Log4Shell emerge, building resilience against malicious cyberattacks is more critical—and trickier—than ever. Adopting cloud-native technologies and open source software makes applications more feature rich and scalable, but it also increases IT complexity. Security teams need their vulnerability management approach to be seamless. Because of this IT complexity, security teams are on the front lines of organizational success and resilience.
In recent years, the number of vulnerabilities has overtaken the ability to effectively monitor IT environments manually. As a result, it’s challenging for organizations to catch up after a DevSecOps transformation, as vulnerabilities proliferate and morph in an environment. Similarly, teams can’t rely on human efforts alone to identify and fix the increasing number of vulnerabilities. Instead, they need to enlist software intelligence to monitor their systems end to end to identify and prioritize remediation efforts.
 |
Cloud operations and observability boost resilience for American Family – blog
Many organizations are investing in multicloud, making improving cloud operations critical. Learn how American Family Insurance implemented Dynatrace to increase resilience. |
 |
Build a proactive approach to cloud operations for increased resilience – Perform 22 session
In this session, learn why and how American Family Insurance implemented Dynatrace to support hundreds of cloud accounts to provide multiple teams with the value from Dynatrace AI. |
 |
Software intelligence as code enables tailored observability, AIOps, and application security at scale – blog
Learn how to easily incorporate software intelligence capabilities into applications’ lifecycle and apply service-level objectives (SLOs) for critical metrics, including performance, quality, and security while adhering to operations standards. |
 |
Dynatrace introduces automatic vulnerability management for PHP open source scripting language – blog
By automatically identifying the most critical vulnerabilities and providing code-level detail and prioritization based on business impact, DevSecOps teams can manage threats and reduce enterprise risk. |
 |
Dynatrace Application Security extends automatic vulnerability management to .NET – blog
Dynatrace extends the coverage of its Application Security module to .NET applications and enables DevSecOps teams to react quickly and ensure the security of digital services and business-critical applications. |
Open source software security
Don’t trade flexibility and features for vulnerability. As organizations adopt cloud-native and open source technologies, their environments become more flexible. However, these technologies can increase complexity. Cloud environment toolkits —microservices, Kubernetes, and serverless platforms — enable business agility, but also create complexity for which many security solutions weren’t built for.
Additionally, real-time visibility into production vulnerabilities helps to secure sensitive consumer and employee data. Today, organizations can move faster and innovate more easily through software development. But some of this agility involves enlisting third-party code libraries that can also contain vulnerabilities. If undetected, these threats can wreak havoc once applications are live and in production. Consider, for example, the recent Log4Shell and Spring4Shell vulnerabilities.
According to recent data, the average time to identify and patch a vulnerability can be more than 200 days. How can organizations get ahead of runtime vulnerabilities before they affect sensitive data?
 |
What is Log4Shell? The Log4j vulnerability explained (and what to do about it) – blog
The Log4j vulnerabilities have triggered millions of exploit attempts of the Log4j 2 library. Learn all you need to know about Log4Shell. |
 |
How Dynatrace uses Dynatrace to combat the Log4j vulnerability (Log4Shell) – blog
As a result of the Log4j vulnerability, the Dynatrace security team explains how they use the Dynatrace platform to stay ahead of the impact. |
 |
Identify and minimize production risk of Log4Shell – blog
For many organizations around the world, time is of the essence to mitigate the vulnerability in the Apache log4j 2 library. Learn the top three criteria to prioritize. |
 |
Log4Shell highlights the need for secure digital transformation – blog
Modern observability and vulnerability management gave Avisi the secure digital transformation strategy they needed to conquer Log4Shell. |
 |
Spring4Shell: Detect and mitigate new zero-day vulnerabilities in the Java Spring Framework – blog
Spring4Shell vulnerabilities expose Java Spring Framework apps to exploitation. Learn what Spring4Shell is and how to detect and mitigate it. |
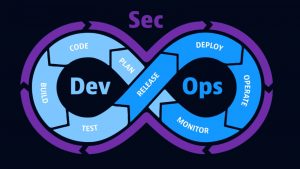
DevSecOps: Security by design
A core principle of DevSecOps practices and culture is security by design, which considers cybersecurity at the outset of software development, not as an afterthought. DevSecOps teams need to build security into their development plans earlier in the software development lifecycle to enable code testing for vulnerabilities—not only in development but also in production.
DevSecOps practices build on DevOps, ensuring that security concerns are top of mind as developers build code. Integrating security into the DevOps workflow helps organizations improve their application security, so they can better protect users and businesses from cyberattacks and data breaches. For example, advanced DevOps observability tools that incorporate DevSecOps principles can spot and address dangerous zero-day vulnerabilities, such as Log4Shell, preventing malicious actors from executing commands on certain Java processes that are accessible to the outside world. By automating DevSecOps release validation through quality gates, organizations can even ensure that their releases are secure by default.
 |
What is DevSecOps? – blog
What is DevSecOps? DevSecOps practices connect three different disciplines: development, security, and operations. Learn how security improves DevOps. |
 |
Security as code demands proactive DevSecOps – blog
Learn what “security as code” is, how to build a “security as code” culture, and why organizations must adopt a proactive DevSecOps stance. |
 |
DevOps vs. DevSecOps – blog
Consider how to incorporate security practices into your software delivery workflows, to protect your users and your business. Read more now. |
 |
Automated DevSecOps release validation ensures security by default – blog
In modern cloud-native environments, which rely on microservices architectures, application teams that are responsible for innovation face some dilemmas. |
 |
Log4Shell vulnerability discovery and mitigation require automatic and intelligent observability – blog
Log4Shell made apps and devices worldwide susceptible to attack. Vulnerability monitoring in production must be a priority these days. |





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum