Leveraging Dynatrace with Journald structured logs, you can enhance the observability of modern operating systems and close your Kubernetes monitoring gaps.
In this blog post, you’ll learn how Dynatrace OneAgent® automatically identifies Journald and ingests structured logs into Dynatrace while enriching them with topology and infrastructure context.
Why migrate from Syslog to Journald
Journald provides a more modern alternative that addresses the limitations of existing Syslog implementations. It offers structured logging, fast indexing for search, access controls, and signed messages. Thanks to its structured and binary format, Journald is quick and efficient.
Journald provides unified structured logging for systems, services, and applications, eliminating the need for custom parsing for severity or details. It supports multi-line logs, handles log rotation, and even includes mechanisms to check for data corruption.
Overcoming native Journald limitations with Dynatrace
Journald doesn’t natively support easy log collection and centralization. Unlike rsyslog, which requires minimal configuration for centralization, Journald’s approach, using systemd-based operating systems, necessitates more advanced configurations and additional components.
Dynatrace OneAgent solves this problem by effortlessly detecting and centralizing logs while providing unmatched flexibility, thanks to the Dynatrace platform’s centralized and dynamic ingest rule controls.
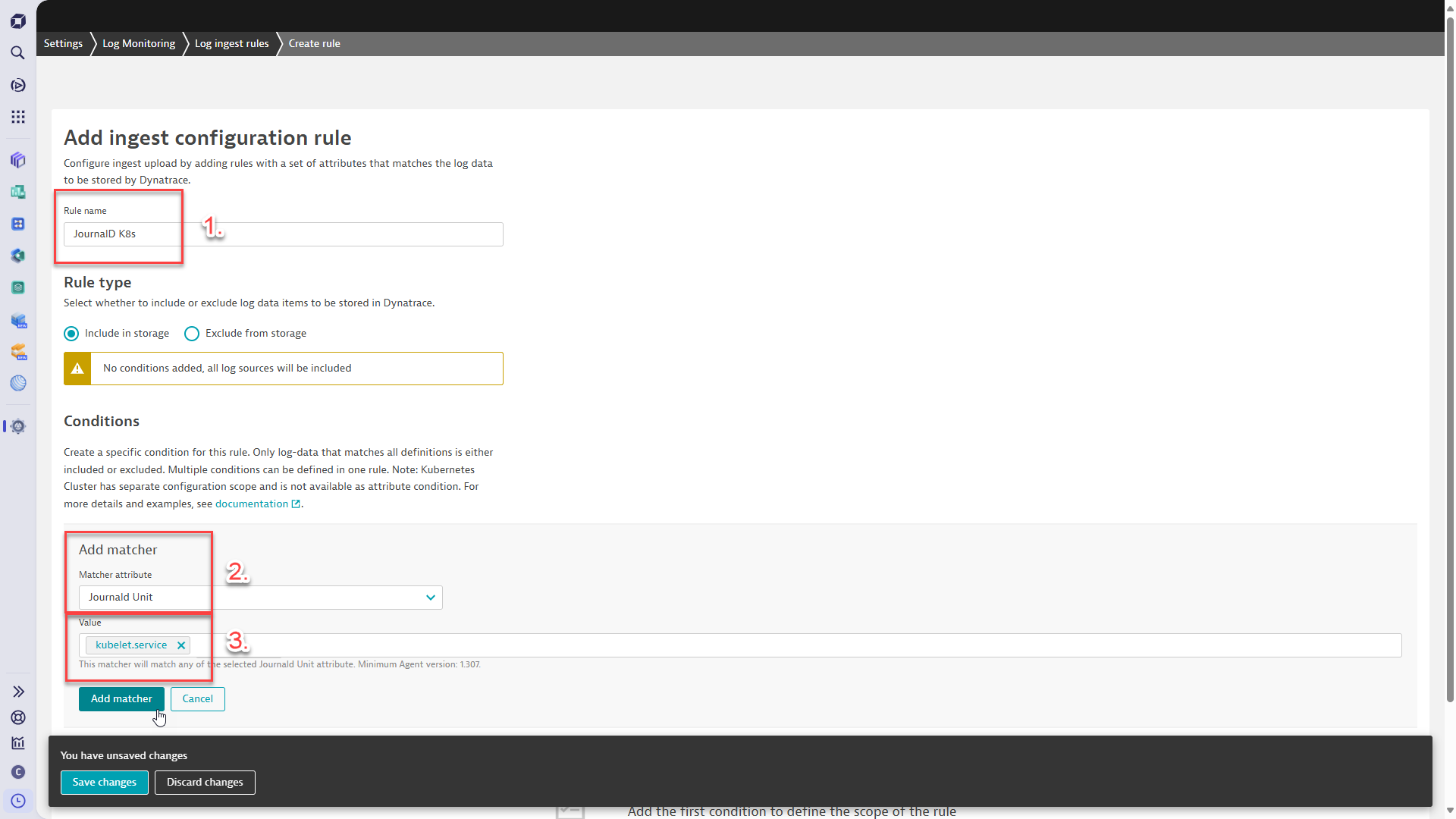
Dynatrace comes with log ingest rules, including a built-in Journald log rule. When activated, this rule facilitates the OneAgent Journald log detector’s collection and ingestion of Journald-related logs.
The configuration is managed centrally within Dynatrace settings (Settings > Log ingest > Log ingest rules).
The Dynatrace platform and settings also allow you to define custom rules, such as defining which Journald units and logs should additionally be included or excluded.
Why unified observability boosts productivity
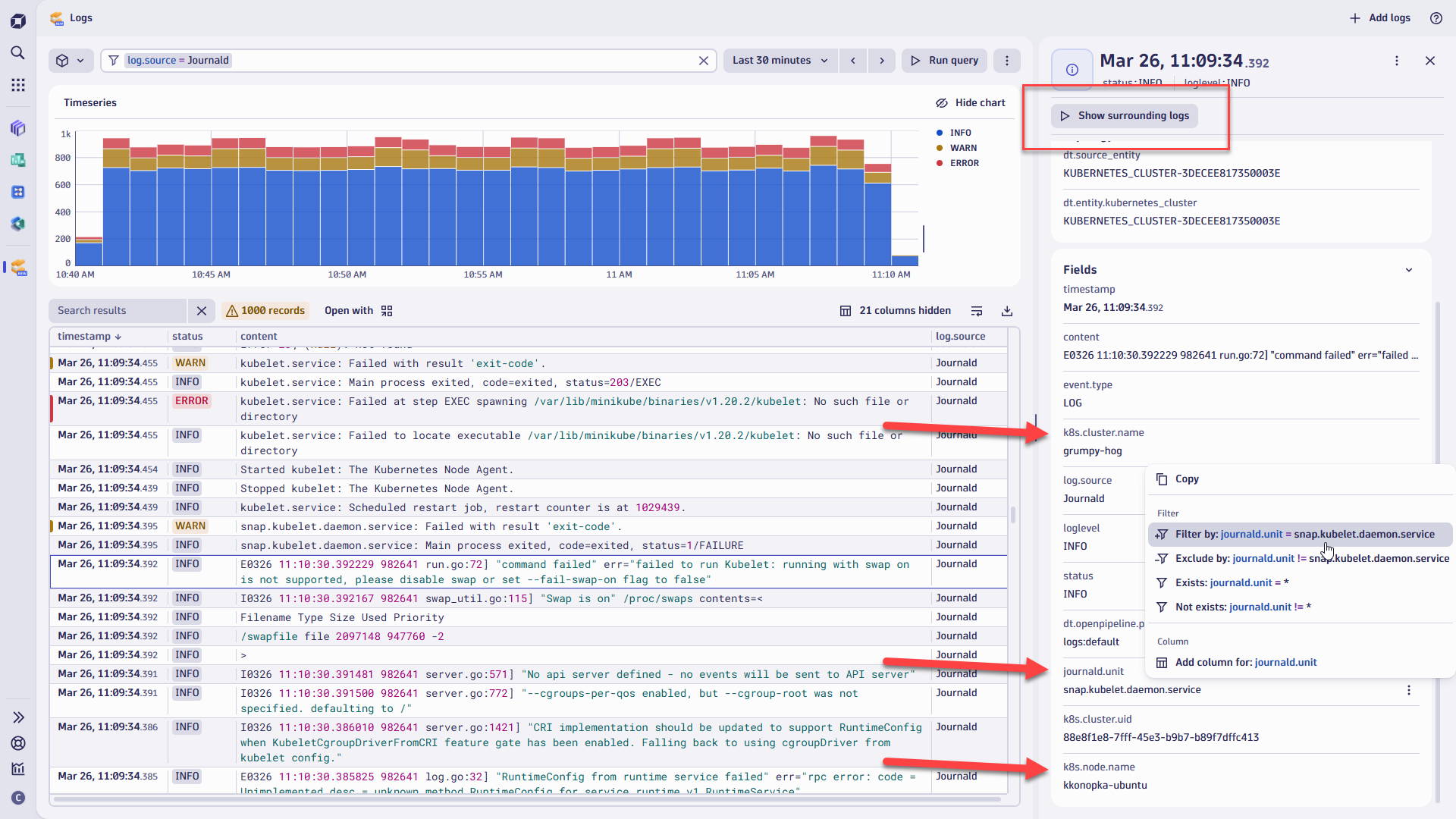
While journalctl is a powerful local tool with local filtering capabilities, it doesn’t scale well, especially considering the globally distributed components of today’s hybrid/cloud-hosted environments. When using Dynatrace, in addition to automatic log collection, you gain full infrastructure context and access to powerful, advanced log analytics tools such as the Logs, Notebooks, and Dashboards apps. For forensic log analytics use cases, the Security Investigator app benefits from the scalability and analytics power of Dynatrace Grail™.
Grail, the Dynatrace schema on-read data lakehouse, is at the heart of the Dynatrace platform. It provides unified observability by automatically correlating logs and placing them in the context of traces and metrics.
Unlike traditional setups that require predefined schemas, Grail allows you to store diverse data types without schema definitions at any point, providing greater flexibility in any analytic situation.
The Grail architecture ensures scalability, making log data accessible for detailed analysis regardless of volume. With real-time analysis, you gain faster data-driven decisions and simplified data ingestion. Dynatrace Grail lets you focus on extracting insights rather than managing complex schemas or index and storage concepts.
Davis® AI works with Grail as part of the Dynatrace platform’s integrated automation and AI capabilities.
System health, performance troubleshooting, and debugging situations no longer require manual correlation of logs across multiple disconnected tools or servers. Thanks to Davis AI’s automatic problem detection capabilities with logs in the context of entities, services, applications, and traces, your root cause analysis efforts are greatly reduced.
Why use Dynatrace OneAgent for Journald
Dynatrace OneAgent automatically ingests logs from Journald, eliminating the need for manual configuration and ensuring comprehensive log coverage while offering centralized and granular rules for log collection. In addition, OneAgent handles log rotation, decompression, and parsing automatically, reducing the overhead associated with manual log management.
With built-in log enrichment, OneAgent adds valuable attributes such as trace and span IDs to log records, facilitating deeper analysis and correlation with distributed traces. Journald logs are integrated into the Dynatrace platform this way, providing a unified view of system and application logs alongside other observability data.
Since you can ingest Journald logs using Dynatrace OneAgent, this feature is available to customers of both the latest Dynatrace SaaS and Dynatrace Managed.
Start collecting Journald logs with Dynatrace today
If you haven’t started collecting Journald logs with Dynatrace, install OneAgent on your systemd-based operating systems and consult Dynatrace Documentation for additional details if you want to configure custom rules to include or exclude specific Journald logs.




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum