Runtime security and system observability are critical to helping organizations eliminate blind spots that undermine effective DevSecOps objectives. Here’s how an observability platform can identify runtime vulnerabilities.
Security blind spots pose a significant threat to an effective DevSecOps strategy and leave organizations vulnerable to attack—in some cases when applications are already live.
In December 2021, the emergence of the Log4Shell zero-day vulnerability demonstrated the potential impact of vulnerabilities in runtime. An effective DevSecOps strategy helps organizations identify vulnerabilities throughout the software development lifecycle (SDLC) to ensure the integrity of software in development and of runtime applications.
Integrating security too late in the SDLC, expanding cloud access, and delayed security testing are just a few examples of security roadblocks to effective DevSecOps.
In a recent session at Dynatrace Perform 2022, Andreas Berger, senior principal project product manager of application security at Dynatrace, and Christian Schwarzbauer, application security product architect, dissected the importance of integrated runtime security and system observability in detecting, identifying, and addressing these blind spots across organizations.
Three key runtime security questions for DevSecOps
To be effective, Berger argues, modern application security requires speed and precision. “This is the core of what all security solutions should provide,” he says. Solutions must keep pace with the quickly changing apps in cloud-native environments. “Security solutions should highlight what really matters without flooding everyone with false alerts.”
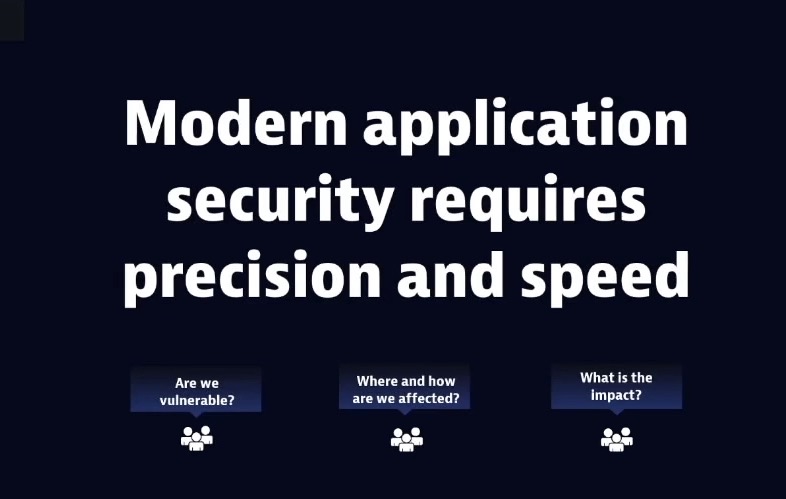
Ultimately, security solutions should help organizations answer three key questions:
- Are we vulnerable?
- Where and how are we affected?
- What is the impact?
Prioritizing alerts in the face of runtime security blind spots
For finding and addressing runtime application security blind spots, a security solution should help you prioritize your efforts. But what does alert prioritization look like in practice?
With Dynatrace Application Security, prioritizing starts with its automatic and intelligent observability platform. Automatic discovery and instrumentation allow businesses to evaluate their entire environment in seconds, discover actionable information, and tap into real-time tracking on all affected processes.
The challenge? Given the depth and breadth of DevSecOps-driven tracking, the number of reported security vulnerabilities is often substantial. So substantial that organizations are often unsure where to focus their efforts.
Berger lays out the following ways Dynatrace helps organizations to prioritize their security vulnerability risks:
- Prioritize individual areas of interest. By combining the full coverage of Dynatrace analysis with extensive search functions, DevSecOps teams can quickly filter vulnerabilities by areas of interest to narrow response focus and address specific issues immediately.
- Prioritize vulnerabilities using automated risk assessment. Automated risk assessment, meanwhile, helps organizations identify vulnerable functions tied to a specific security risk that are currently in operation, exposed to the internet, or designated as sensitive data assets. This automated assessment reports an organization’s overall risk on a scale of 1 to 10 and the number and type of vulnerable functions in use.
- Prioritize issues by vulnerable component. Dynatrace can also prioritize issues by vulnerable components—such as log4j-core or tomcat-enabled-core—that influence multiple processes or functions. The Dynatrace platform shows how many critical vulnerabilities teams can address by upgrading each of these components. This prioritization enables teams to focus their efforts for maximum impact.
Moving DevSecOps beyond continuous WAF maintenance
It’s one thing to detect issues before they happen, but what about handling attacks as they occur?
“While web application firewalls (WAFs) remain the de facto standard for app protection, they are not without their drawbacks,” Schwarzbauer notes. In particular, firewalls could potentially reject authorized resource requests if they are misconfigured.
Schwarzbauer adds another potential drawback. “No matter how strong a WAF is, attackers will eventually find a way inside the network.”
As a result, teams need to continually maintain and manage WAFs to keep evolving risks in check.
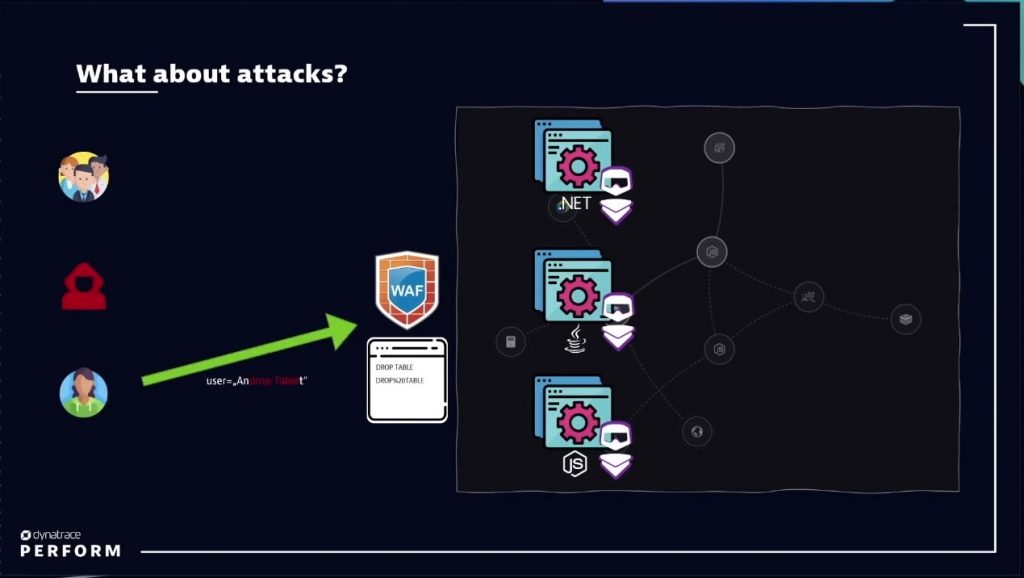
Runtime application security from Dynatrace makes it possible for IT teams to keep pace with attacks as they occur. While also identifying potential threats, their location, and the vulnerabilities they exploit, Dynatrace provides information about the entire attack path. This visibility includes the source IP to entry point, vulnerability type, and eventual database backend target.
Additionally, each stage of the security process specifies the code location and function used by attackers to gain entry. Armed with this information, businesses organizations are better equipped to improve security across the entire DevSecOps pipeline.
Clearing up security blind spots for good
Simply put, by pairing runtime security with system observability, businesses are better prepared to detect, deflect, and defeat emerging security threats.
To learn more about the role of runtime application security and system observability in delivering on DevSecOps objectives, check out the full session, Address Log4Shell with ease: Why integrated runtime security and observability is key for DevSecOps.
And check out our Dynatrace Perform 2022 conference coverage guide here.



Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum