Recently, some organizations fell victim to a software supply chain attack, which led to loss of confidential data. This article explains what a software supply chain attack is, and how Dynatrace protects its customers against such attacks by applying:
- Risk management and business continuity planning
- Security controls in the software development life cycle (SDL)
- Security controls in the delivery and update life cycle
- Independent audits of security controls
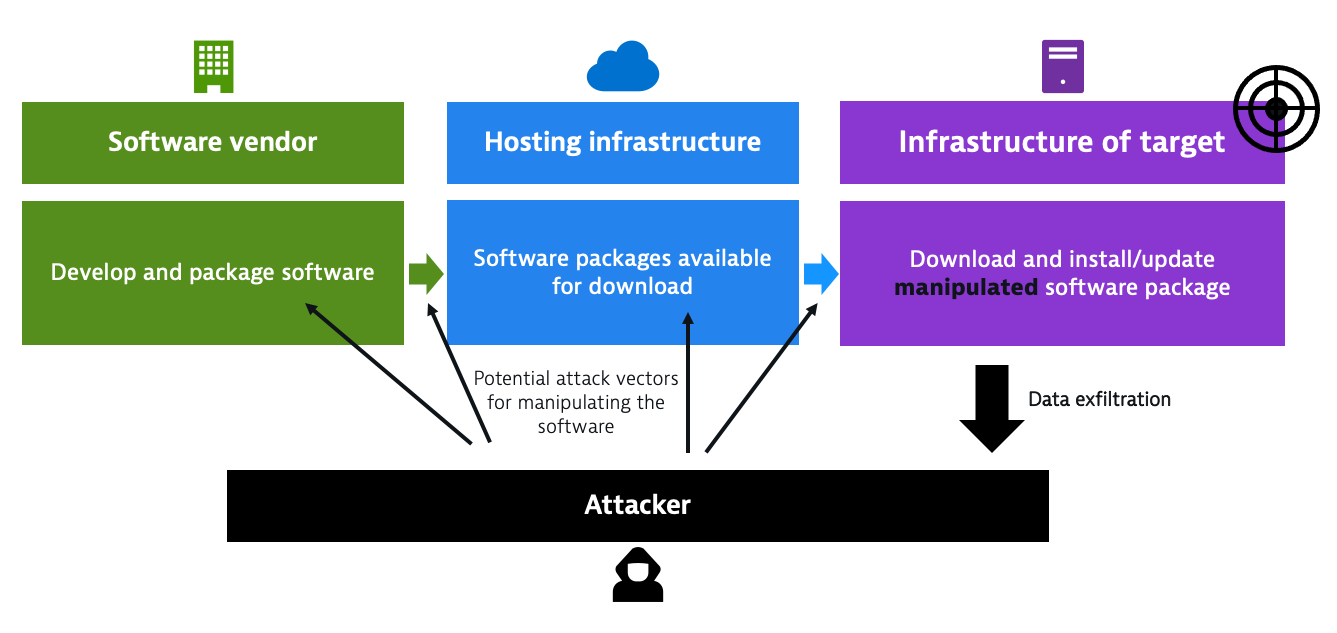
What is a software supply chain attack?
Rather than attacking an organization directly, a software supply chain attack targets the vendor software that’s used by the targeted organization. Typically, the attackers attempt to exploit some weakness in the vendor’s development or delivery life cycle and attempt to inject malicious code before an application is signed and certified. This way the attacker can exfiltrate data from the targeted organization.
Risk management and business continuity planning
Dynatrace tracks worst-case scenarios and business risks as part of its business continuity planning program. From the very first days of Dynatrace development, preventing the injection of malicious code that could potentially compromise customer infrastructure, has been a priority. This has led to the implementation of numerous security controls within the software development life cycle (SDL) as well as the implementation of a variety of secure operation controls.
Security controls in the software development life cycle (SDL)
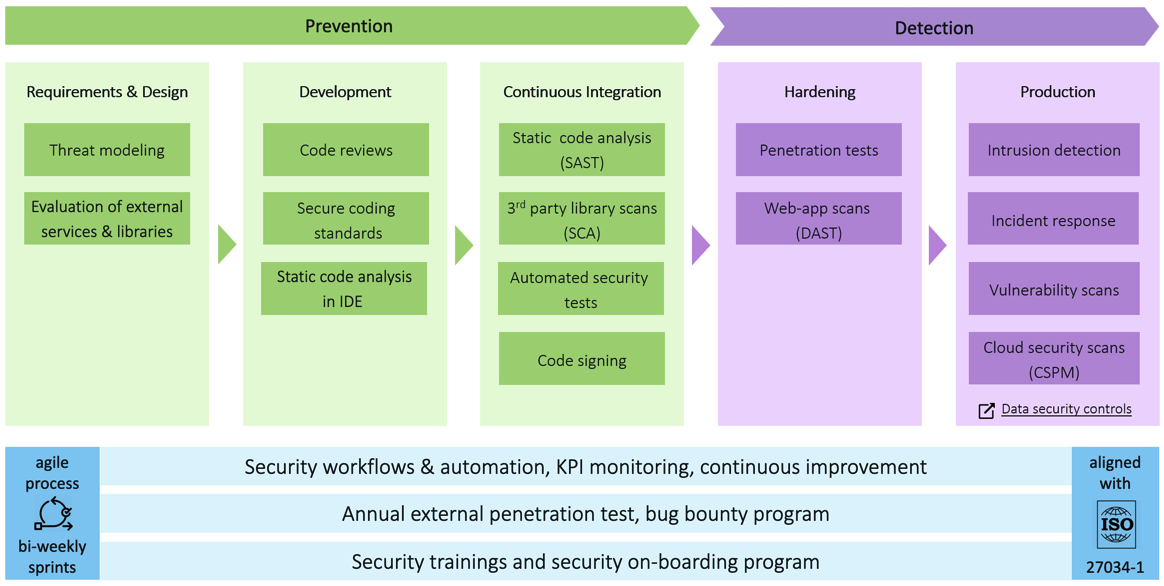
It all starts with the code. Dynatrace has established a secure SDL, which automatically enforces that all developed code is reviewed by a peer. These reviews:
- Automatically scan for vulnerabilities and malware
- Automatically run thousands of automated tests
- Automatically sign and verify during installation
- Ensure manual penetration testing
- Ensure all artifacts are transferred and stored encrypted
- Track changes via our change management process
Access to source code repositories is limited on both the network and the user level. Only authorized users are able to access code repositories and make changes to source code. Source code management systems are only accessible from within the Dynatrace corporate network. Remote access to the Dynatrace corporate network requires multi-factor authentication (MFA).
The full list of secure development controls, along with many more details, are documented at Dynatrace secure development controls. The diagram below provides an overview.
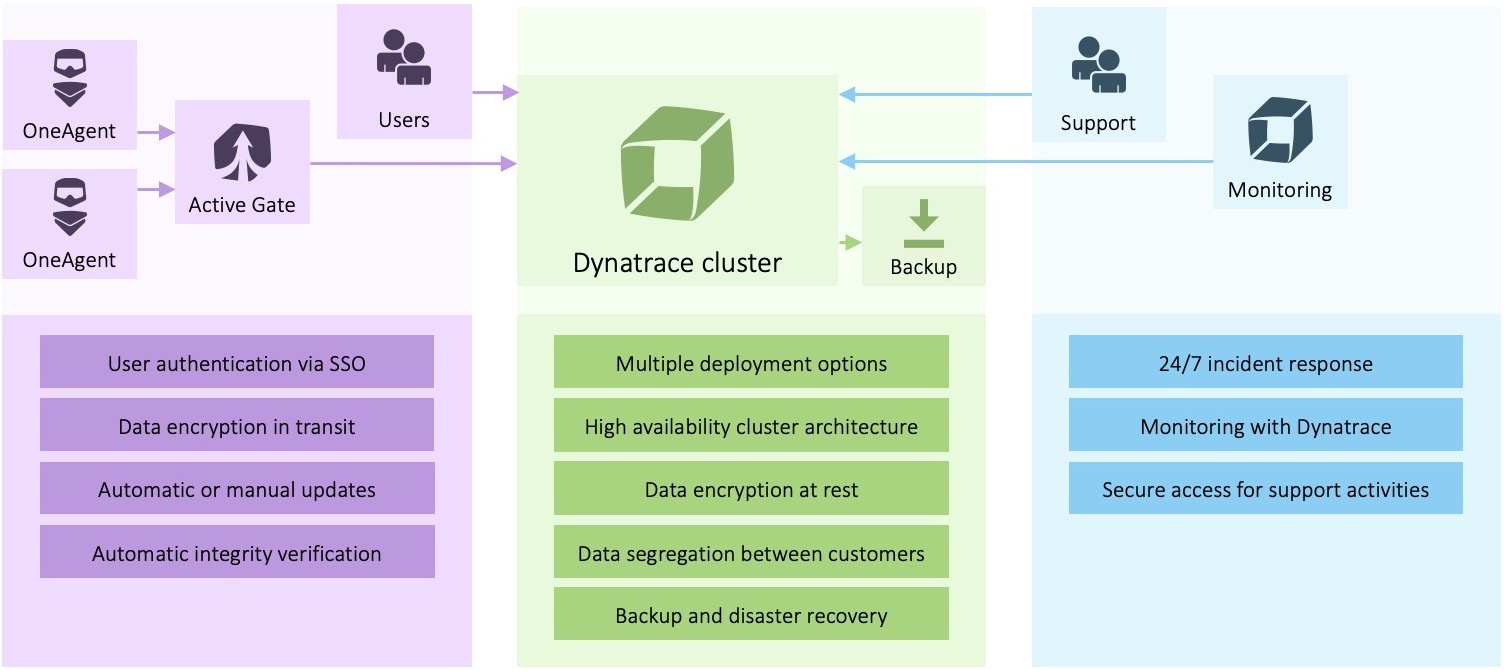
Security controls in the delivery and update life cycle of Dynatrace software components
Dynatrace has implemented several specific security controls and uses industry best practices to protect Dynatrace software components like OneAgent, ActiveGate, and Dynatrace Cluster installation packages from malicious manipulation by attackers on the way to our customers’ infrastructure.
All steps are fully automated, from source code being compiled to binaries, to the upload of the binaries to the AWS infrastructure where they are available for customers to download. No manual, error-prone steps are involved. Communication involving data in transit is encrypted using the latest industry standards (TLS 1.2). Every storage location involving data at rest is encrypted as well.
All installation packages are automatically scanned for malicious software before they’re uploaded to AWS. They’re also signed with a digital code-signing certificate. These certificates are stored on physical devices which are plugged into specifically hardened build servers. The signatures are automatically verified during the update process on the customer infrastructure. If a verification fails (for example, due to installation package manipulation by an attacker), the update process is stopped. Without having access to the physical devices that contain the code-signing certificates, compromise of the binaries is impossible.
A full list of data security and secure operation controls, along with many more details, are documented at Dynatrace data security controls. The diagram below provides an overview.
Independent audits of security controls
The security controls presented above are audited on an annual basis by independent security assessors. Annual SOC 2 Type II certification validates that the security controls are properly implemented at Dynatrace. Annual independent penetration tests are performed as well, which prove the effectiveness of our security controls with a low number of findings. All these audit reports are available to be shared with Dynatrace customers under NDA.
Continuous improvements
Dynatrace has established a continuous security improvement process where security controls are constantly being added, improved, and evaluated.
The new Dynatrace Application Security solution plays a key role in further strengthening the Dynatrace internal security posture, which protects our customers from even the most sophisticated cyber attacks.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum