Whether a developer in your organization needs access to a sensitive project or a Site Reliability Engineer (SRE) needs full admin privileges for a production environment, fine-grained access control is a prerequisite for modeling requirements, permissions, and user roles. Such access controls are now generally available for Dynatrace Cloud Automation.
Along with single sign-on (SSO), granting users permissions based on their role within your organization—an approach known as Role-Based Access Control (RBAC)—is a key capability of tools that require enterprise-wide adoption. While SSO has been available for Dynatrace Cloud Automation since day one, the latest update enables Dynatrace user management for RBAC in the Cloud Automation module—it’s now possible to define, for example, an administrator with full permissions, a user with elevated permissions, or a user with basic view permissions.
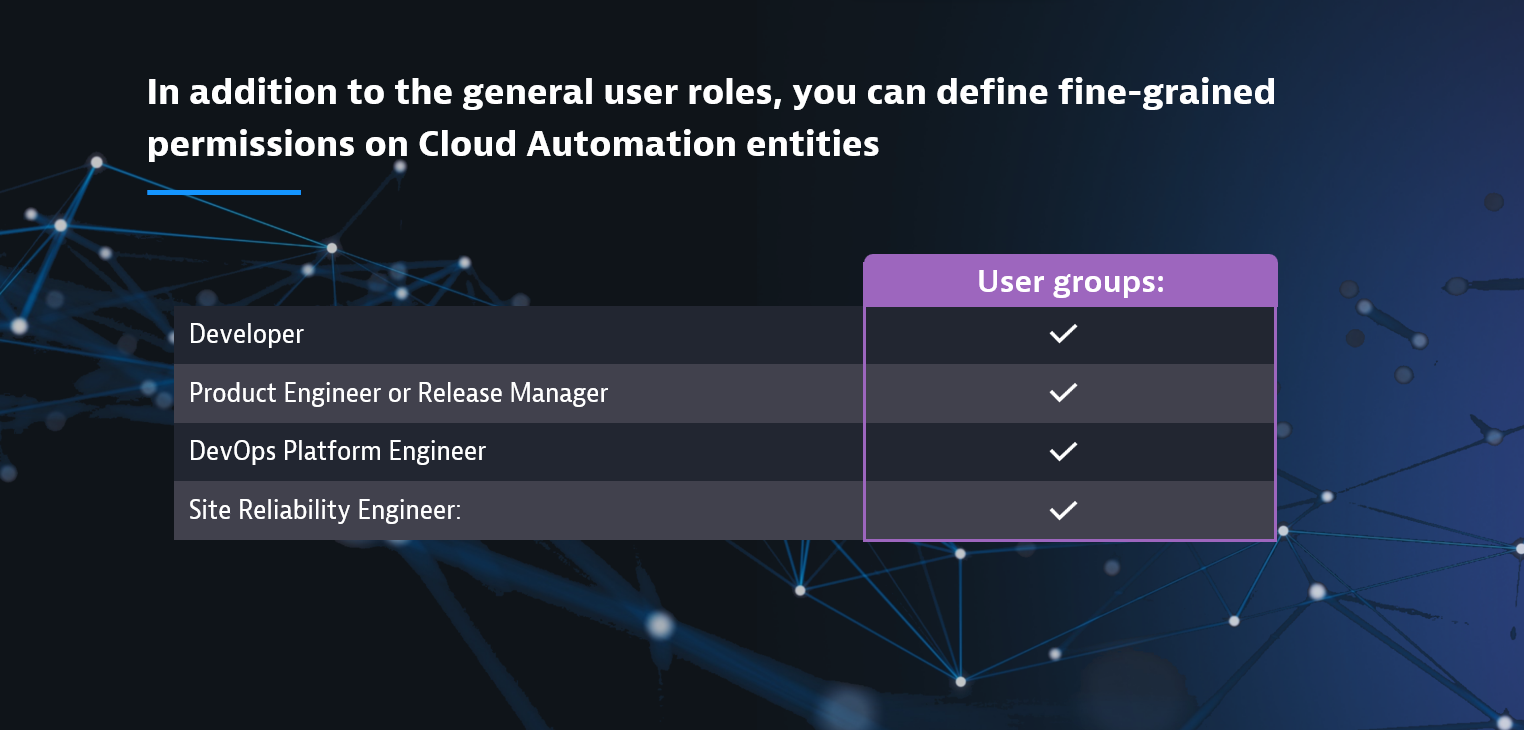
In addition to the general user roles, you can define fine-grained permissions on Cloud Automation entities. This is important for DevOps, Platform Engineers, and Site Reliability Engineers (SRE) who derive their requirements from the Software Development Lifecycle (SDLC) they manage. Given this capability, you can now define user groups such as:
- Developer: Permission to deploy or test a service in a particular project that’s in development
- Product Engineer or Release Manager: Permission to approve the release of applications into the hardening stage for load testing, or into production for end-user usage
- DevOps Platform Engineer: Permissions for establishing tooling at all points in the SDLC
- Site Reliability Engineer: Permissions to set up and trigger remediation actions in production to remain in compliance with defined SLOs
Considering the entire tool stack of today’s SDLC, RBAC is useful for managing, for example, which team members can configure the integration and range of action of certain tools. In other words, RBAC addresses the current limitation that it’s not possible to provide control over the tools that are leveraged for delivery or operational Cloud Automation workflows. In addition to more control over tooling, RBAC is also key to controlling who is allowed to perform which tasks with integrated tools. With RBAC support, your leadership team can maintain control over who has admin permissions and who is allowed to promote software releases to production.
Set up RBAC for Cloud Automation in three steps
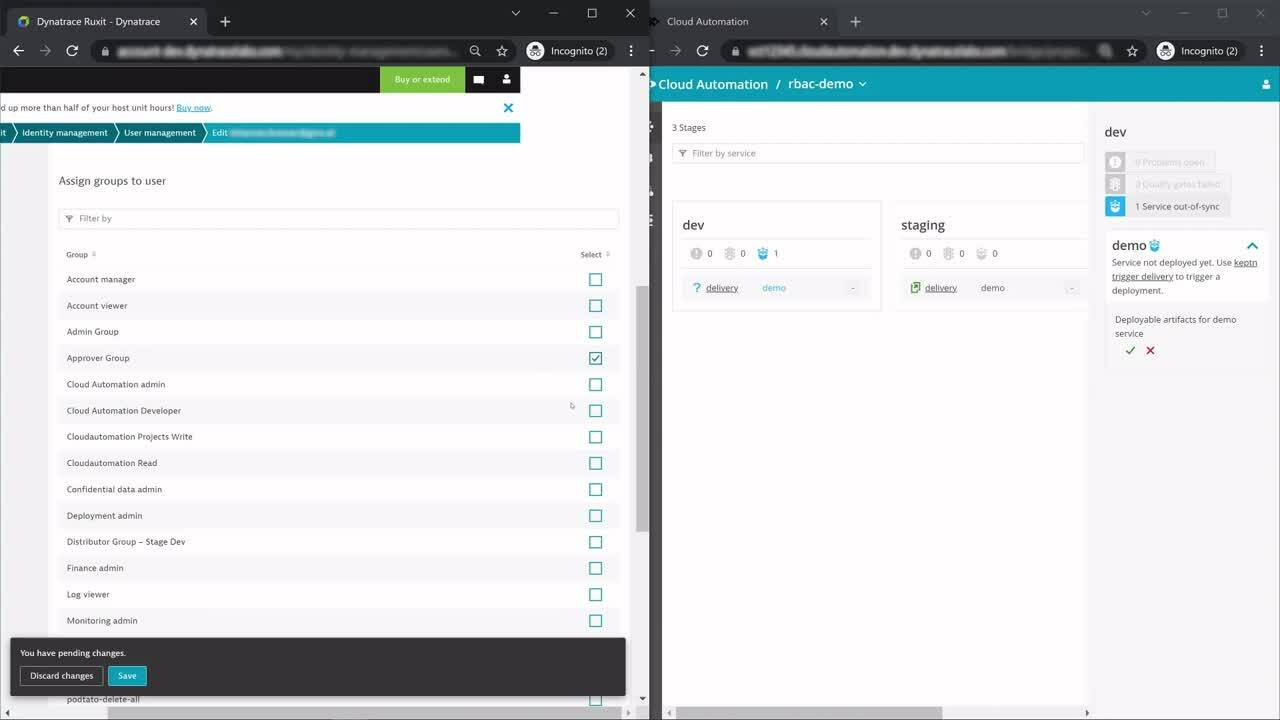
To leverage the new RBAC capabilities for user and group management in your Cloud Automation instance, in the Dynatrace web UI, open the user menu on the menu bar and select Account settings. The Identity management page provides the three steps to configure RBAC. The three steps are Policy management, Group management, and User management.
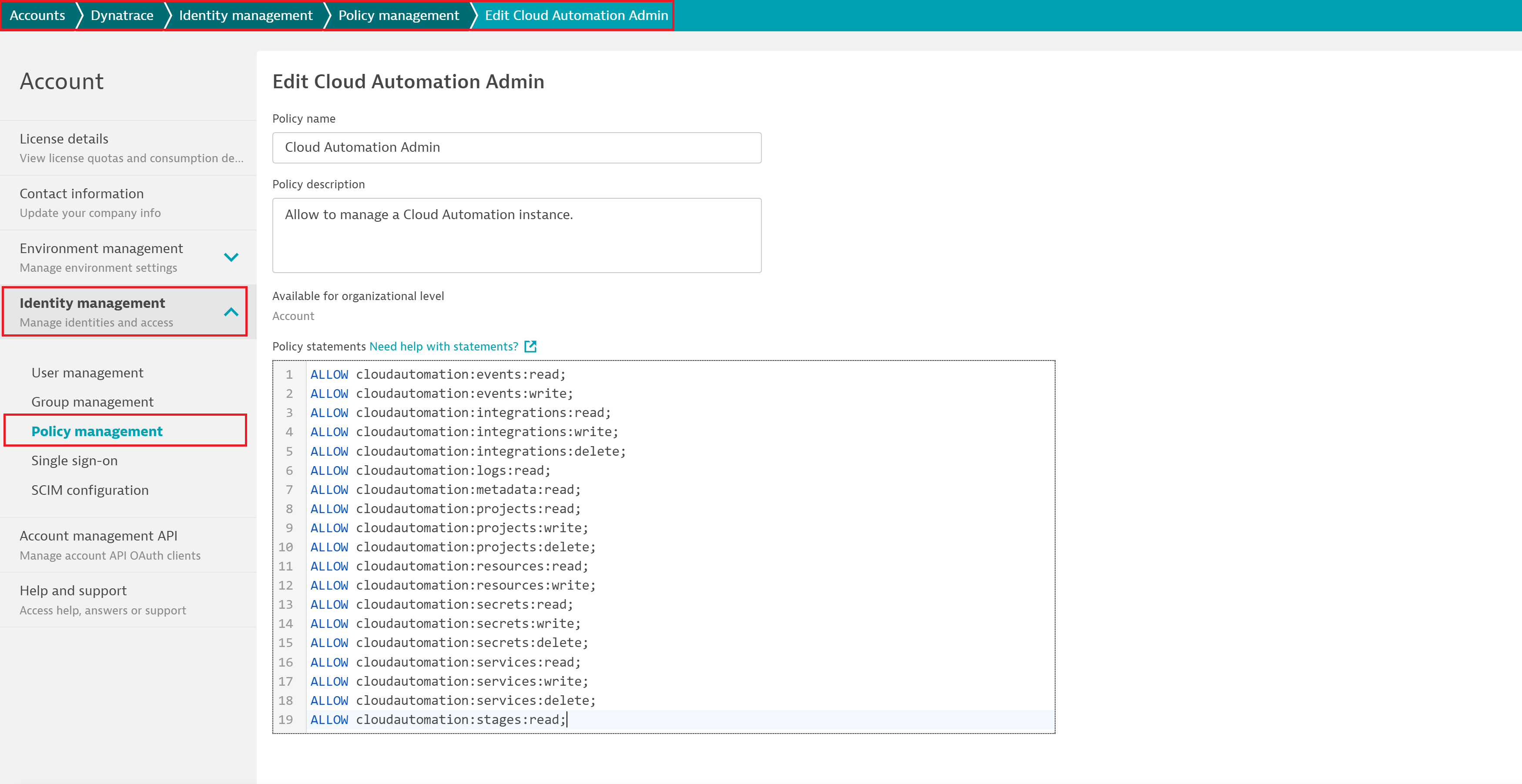
Policy management: The first step is the definition of policies. Dynatrace Identity and Access Management (IAM) provides a native policy definition language. For complete details, see IAM policy management documentation. In the case of Cloud Automation, the same policy definition applies and additional granularity can now be scoped. For instance, the scope for a Cloud Automation project, stage, service, and more can be set to write or read-only. In addition, conditions allow you to limit the scopes on particular values. This means that it’s possible to filter, for example, projects to a particular project by specifying: WHERE cloudautomation:project="easytravel".
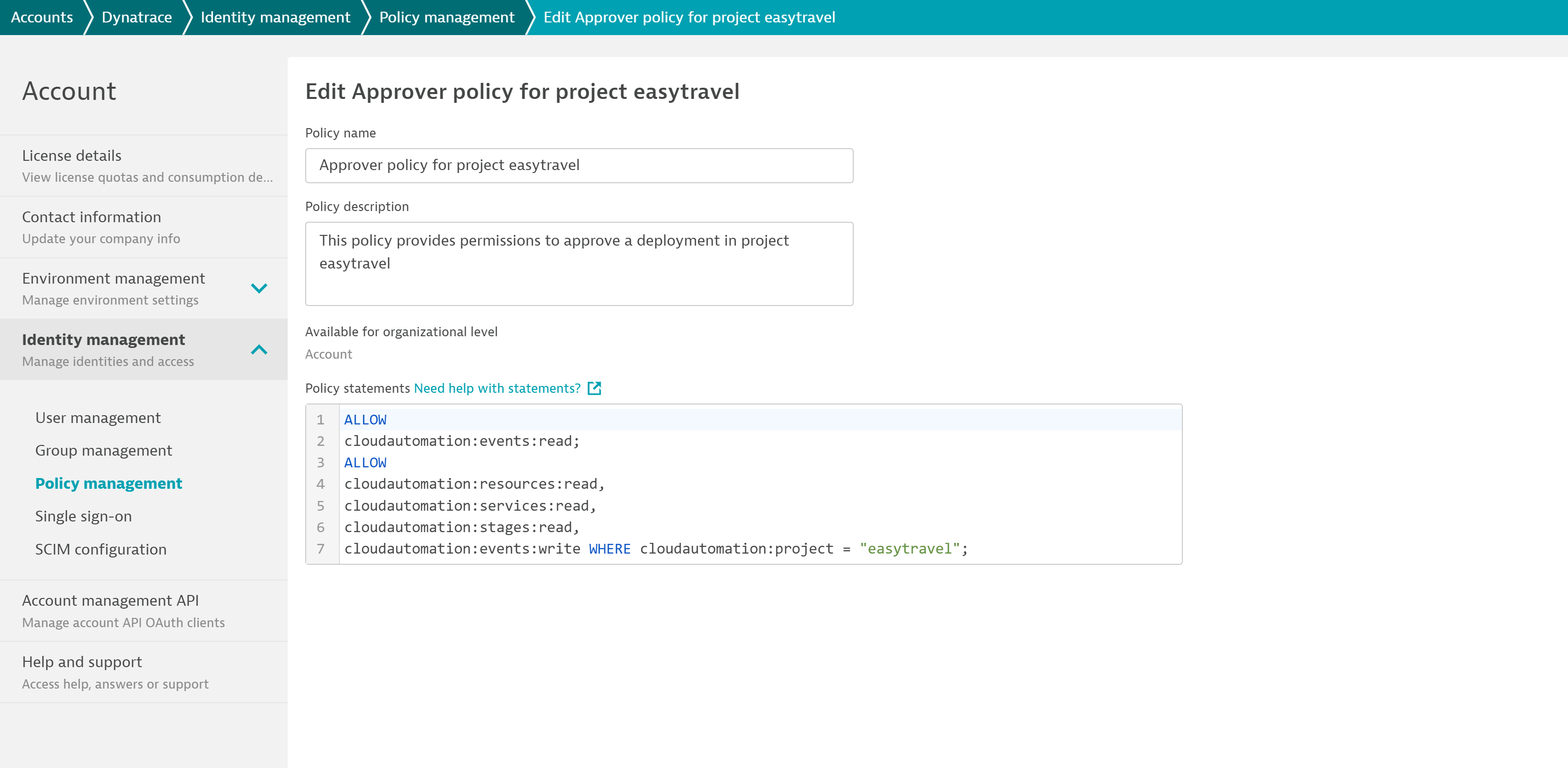
Please consult our user permissions documentation for the full list of Cloud Automation entities, your options for defining conditions, and further policy examples for different user groups.
- Group management: After creating policies, the definition of groups for your organization is required. This depends on your organizational structure and the details of user groups within the SDLC. A best practice example is defining a dedicated group of users who are allowed to view projects, approve certain tasks, or have full admin permissions.
- User management: Lastly, users need to be assigned to the group to receive the granted policies. Upon re-login to the Cloud Automation instance, the users will receive the permissions as defined by the policy.
With RBAC now generally available for any Cloud Automation instance, you—as an administrator of a Cloud Automation instance—can configure user groups and their permissions to work with the Cloud Automation instance, providing you full control over who is allowed to perform specific actions and functions.
Start modeling your RBAC requirements today
The functionality for implementing Role-based Access Control (RBAC) for a Cloud Automation instance is available now. You can either start modeling user roles directly in Dynatrace Identity and Access Management (IAM) or you can consult our IAM policy documentation.
If you aren’t using Dynatrace Cloud Automation yet, enabling the Cloud Automation module is easy—simply reach out to your Dynatrace Product Specialist or our sales experts.
If you need expert guidance and support throughout your company’s digital transformation, our Innovation Services team can help you translate your strategic vision into an executable action plan.
With a recent update of Cloud Automation, the above-mentioned policies for an administrator with full permissions, a user with elevated permissions, and a user with basic view permissions are now automatically created. Consequently, you can start modeling your Role-based Access Control (RBAC) requirements by leveraging these default policy templates. While we don’t recommend modifying these templates, you can customize a copy to suit your needs. Please consult our documentation for Cloud Automation user permissions for more details.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum