Dynatrace delivers cross-container-registry security findings, visibility, orchestration, and prioritization.
Dynatrace, powered by OpenPipeline™, offers a single pane of glass that consolidates container security findings from your existing DevSecOps tools, providing a comprehensive runtime context-based prioritization. It helps unveil blind spots by identifying and addressing coverage gaps throughout your Software Development Lifecycle (SDLC). With contextual operationalization, you can prioritize, visualize, and automate the response to container findings, all within the context of runtime operations while reducing alert noise in the SDLC. Moreover, seamless integration is achieved through out-of-the-box solutions that connect, transform, and map your findings data into a unified format using the Dynatrace Semantic Dictionary, ensuring a smooth and efficient security workflow.
The challenge we’re tackling arises from multicloud environments, where container images are dispersed across different registries and scanned by various vulnerability scanners, if at all. This leads to container security findings scattered across multiple products, complicating achieving unified visibility. The consequences include time spent navigating various platforms to collect data, difficulty prioritizing findings from disparate tools, coverage gaps with containers deployed unscanned, and excessive manual effort required to notify stakeholders and generate tickets.
Addressing this issue is crucial for cloud architects, who aim to establish a robust container scanning process within the SDLC, ensuring timely action on findings and prioritization of critical vulnerabilities. Cloud architects also seek to minimize manual efforts in managing each finding. Meanwhile, developers need prompt notifications about new critical vulnerabilities affecting containers that they can trust and take action on without being overloaded by false positives, which lead to alert fatigue and risk critical alerts being ignored. Developers should handle as few tickets as possible, focusing on those that yield the maximum return on investment (ROI).
Why Dynatrace?
Container security in DevSecOps typically focuses on the build phase, where scanners flag numerous critical vulnerabilities without considering runtime context, often resulting in false alarms. Dynatrace revolutionizes this process by utilizing its insights into active containers and their operational significance. This allows you to prioritize genuine threats impacting live containers. Additionally, Dynatrace observability data for running containers, enriched with security insights, offers a comprehensive view for more effective issue resolution. In essence, Dynatrace refines container security management by integrating runtime context, thus elevating the prioritization and handling of vulnerabilities.
Generic ingest security endpoint
Dynatrace introduces a generic ingest security endpoint, a versatile feature that enables data ingestion directly from any third-party security tool.
This capability opens up a range of use cases, such as:
- Security findings visualization on custom dashboards tailored within Dynatrace.
- In-depth analysis of security findings using tools like Notebooks and Security Investigator.
- Automated orchestration of security findings through Dynatrace Workflows, enhancing efficiency and response times.
- Contextualization of third-party security findings with Dynatrace runtime entities, offering a more integrated and coherent security management experience.
With the generic ingest security endpoint, you can ingest any data in an unstructured format. However, to truly gain the benefits of uniform prioritization, the ideal scenario is to have the data in a unified format. To this end, we’re also releasing Dynatrace Semantic Dictionary conventions for vulnerability findings.
The Dynatrace Semantic Dictionary for vulnerability findings is a key feature in Dynatrace that enables a consistent and uniform analysis of security data. Dynatrace uses this format in supported third-party integrations, but this same format can also be used to map data from custom integrations.
It allows for uniform prioritization of container vulnerability findings across different tools, which can be conveniently managed and visualized through Dynatrace sample dashboards.
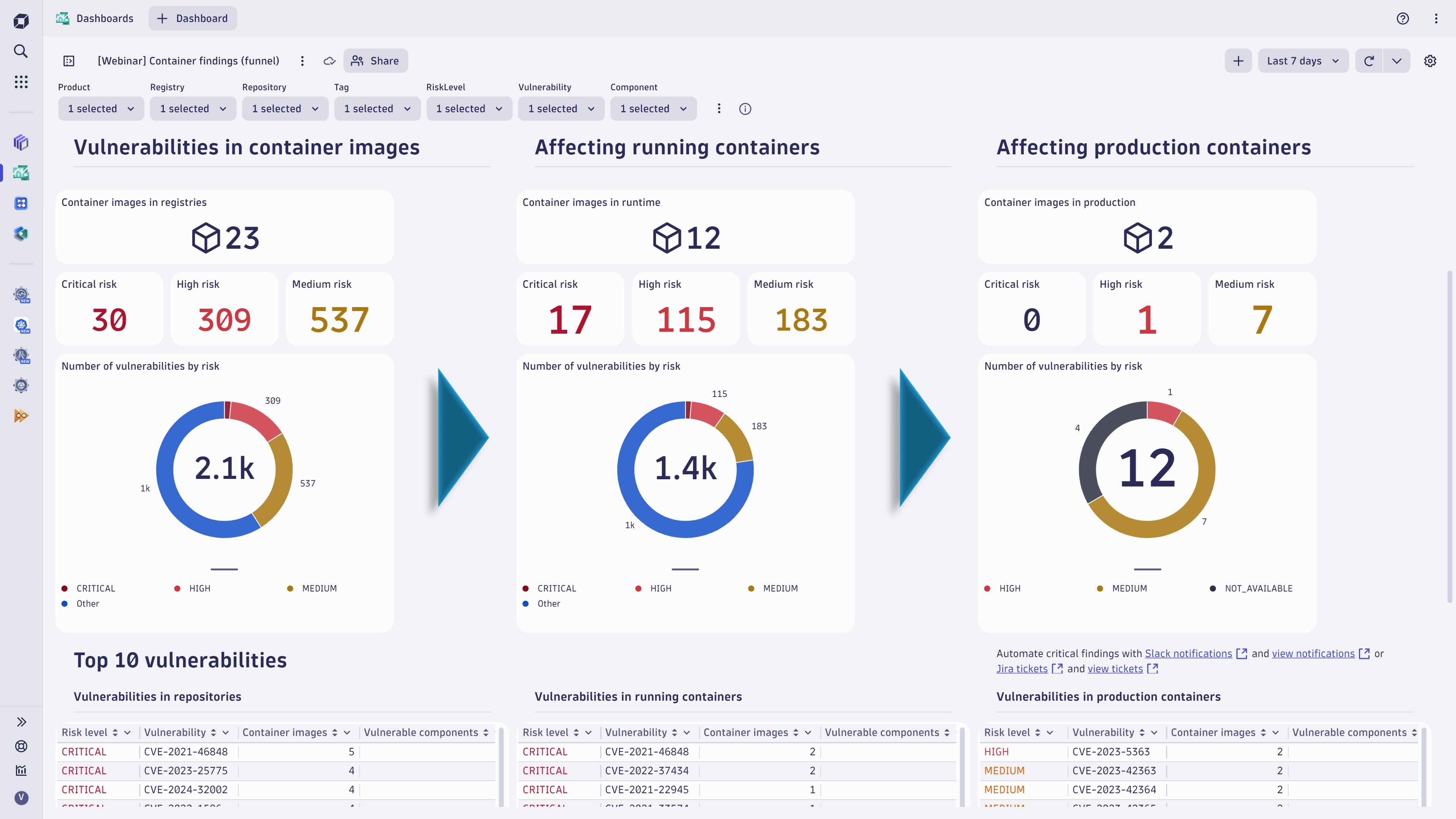
Additionally, this format supports automated notification of vulnerability findings across security tools, utilizing Dynatrace sample workflows to enhance efficiency.
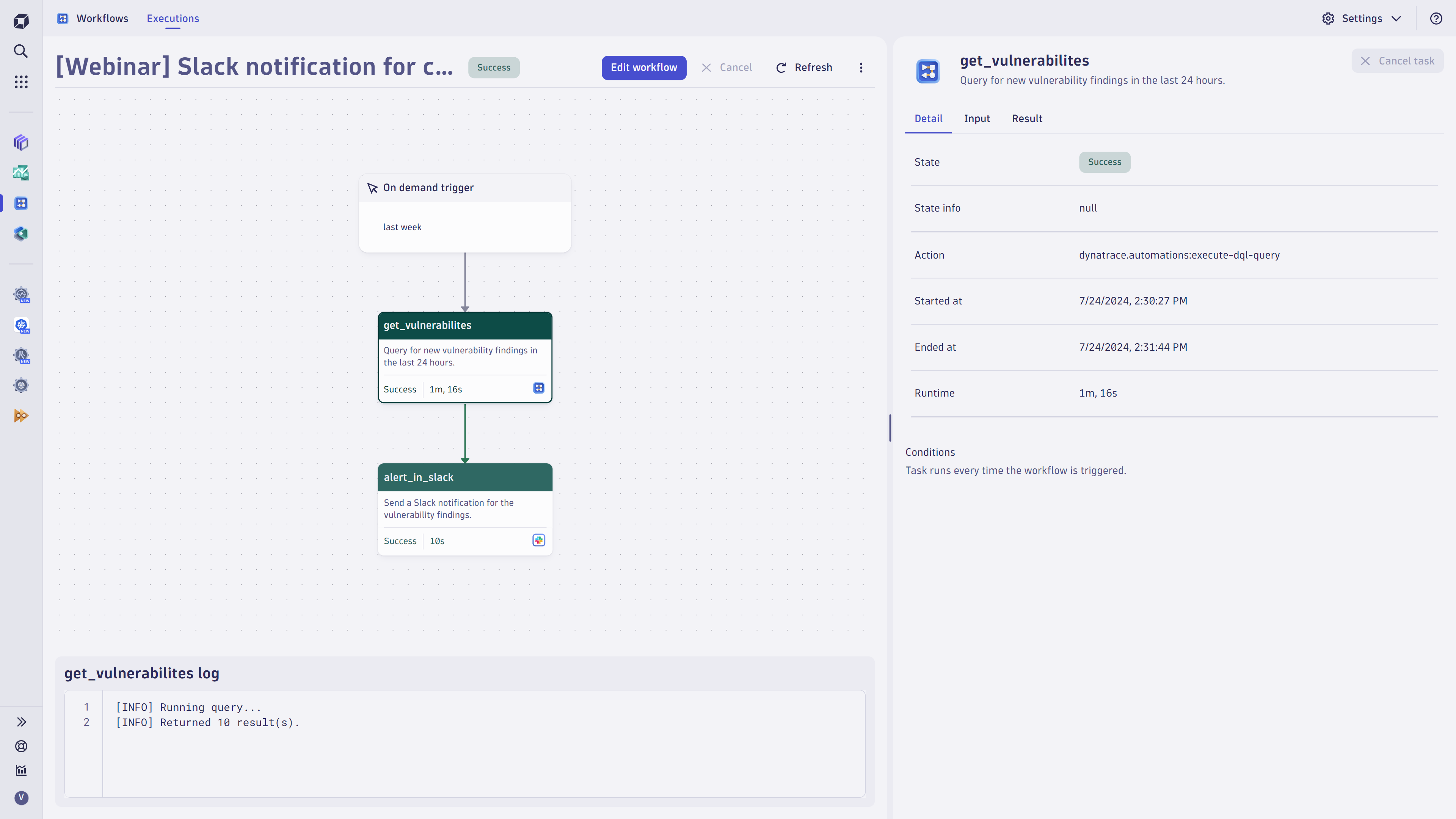
Lastly, the generic ingest security endpoint provides a comprehensive understanding of the security findings coverage within your runtime environment, ensuring that all potential vulnerabilities are accounted for and addressed. This unified approach ensures that security management is systematic and effective, catering to the complex needs of modern containerized environments.
Dynatrace supported integrations
Dynatrace supported security data ingest integrations streamline the setup process and ensure automatic Semantic Dictionary (SD) mappings, providing a seamless integration experience.
With the first integrations in place, the foundations are there to build additional native integrations into the Dynatrace Platform to support additional container registries and generic security standards. This will expand our capability to provide contextual information to observability and security events, irrespective of where they originate. So, look for future blog announcements on this topic.
What’s next
- Watch the data-driven DevSecOps automation webinar, where we present and discuss the benefits of Dynatrace runtime context in operationalizing third-party security findings.
- To discover which products, tools, and standards we support, please visit the Dynatrace Hub.
- Explore the security data ingest capabilities and view the step-by-step setup guides for the supported integrations in Dynatrace Documentation.
- For additional out-of-the-box integration requests, please contact your Dynatrace account manager or submit a request in the Dynatrace Community.




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum