Dynatrace recently joined forces with Hackerone, the industry leader in external bug bounty programs.
Customers deserve to use a secure product, and Dynatrace has continuously upgraded its game in improving the security of its software. We’ve recently joined forces with Hackerone, the industry leader in external bug bounty programs. For us, this is a logical next step after running our own internal bug bounty effort in 2018 to enhance security.
Wait, what is a bug bounty program?
According to Hackerone a bug bounty program is described as:
A program where ethical hackers are invited to report security vulnerabilities to organizations, in exchange for monetary rewards for useful submissions. Bug bounties are commonly seen as the most effective and inexpensive way to identify vulnerabilities in live systems and products.
Why does it matter to me as a customer?
As cyber threats are rising, it’s becoming more and more important for us to invest in the security of the product we offer to customers. Dynatrace stands for high performance and only wants to ship a product that adheres to the highest security standards in the market.
We achieve this by putting a huge effort into improving our SSDLC (Secure Software Development Lifecycle). Parts of our SSDLC include:
- Daily code-level security scans at the time of ongoing development.
- Secure code reviews by team members with great expertise in avoiding security pitfalls.
- Internal penetration tests before new features are released.
- Annual external penetration tests that cover the entire product.
- …and much more.
Over and above this, it’s become highly important that we expand the crowd of hackers who are looking for potential security flaws. We, at Dynatrace, evaluated a couple of options in the field of security offerings and decided to go with Hackerone. We were really enthusiastic to see that they have more than 200,000 computer security analysts hunting down bugs.
Dynatrace is confident that this new approach will create an additional layer of defense against cyber attacks, which should reinforce the already strong trust in our products.
Got it! Now I’m intrigued—how does Hackerone work?
It all starts by registering with Hackerone. A security researcher would go straight to their website and create a profile. They can then browse for all public bug bounty programs to participate in.
Dynatrace, however, operates in private mode currently. This means that an aspiring researcher must receive an invitation first in order to be allowed to submit potential vulnerabilities to Dynatrace. This approach has been recommended by Hackerone for the first few months. We kicked off our program in April 2019, we’ll continue to operate in private mode for the better part of 2019.
Once a bug bounty hunter is invited, they can hack all Dynatrace components that are in the program scope. If they find a potential vulnerability, they hit the submit button and send over a detailed description of the bug.
Sweet, but why would security researchers participate in Dynatrace’s Hackerone program?
Bug bounty programs are set up to reward external researchers with sums of money for each valid submission. Dynatrace offers different monetary rewards based on the severity of the vulnerability found.

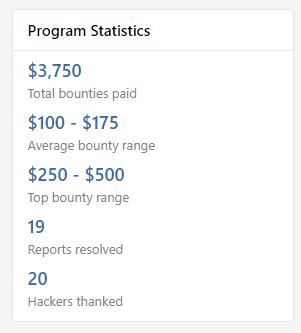
Once we’ve agreed on the severity of a finding with the security researcher and Hackerone’s triaging team, we initiate the bounty payout with the click of a button. In the first two months of our bug bounty program, we’ve paid out $3,750 to about 20 different security researchers.
That’s awesome, but how does Dynatrace handle hacker submissions?
First, we have Hackerone’s premium triaging support. This means that several security experts working for Hackerone triage each individual submission before we are notified. If the finding turns out to be a true positive, Dynatrace’s security team comes into play.
At this point, we run a second round of triage in an attempt to exploit the found vulnerability in different development stages. Next, we create Jira tickets for our respective developers and help them remediate the findings as quickly as possible.
By now, our bug bounty program has already become an integral component of our SSDLC (Secure Software Development Lifecycle).
What’s the long-term plan for the program?
We’re currently working on amplifying the Dynatrace bug bounty program to attract more researchers:
- We’ll extend our testing environment by setting up more individual accounts, which we can distribute to security researchers who want to participate.
- Next, we’ll put additional domains and components in scope so that researchers will have a wider field.
- In the long term, we’ll gradually raise our bug bounty rewards.
- Finally, we’ll open the program to the public, allowing everybody on Hackerone to submit to Dynatrace.
Conclusion
We, at Dynatrace, are doing everything we can to improve the security posture of our product. We now also rely on and receive help from an armada of external security researchers in addition to all the security controls we ourselves implement as part of our SSDLC (Secure Software Development Lifecycle).





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum