Enhancing security insights and threat intelligence data in our platform, Dynatrace integrates with Microsoft Sentinel.
Secure your hybrid cloud environments at runtime with Dynatrace using runtime vulnerability analysis, AI-assisted prioritization, runtime application protection, and log audit and forensics. Integrating with Microsoft Sentinel adds security events to our Runtime Application Protection and provides additional data for investigation with our security analytics features using Dynatrace Query Language on Grail.
Integrating existing point tools empowers DevSecOps teams to identify and mitigate emerging threats by using Dynatrace’s platform approach to security featuring advanced real-time attack and vulnerability detections powered by Davis AI. Dynatrace provides a continuous unified view of relevant security events fully integrated with our SmartScape technology.
Dynatrace Application Security provides automated runtime vulnerability detection and risk assessment for cloud-native applications across the entire software development lifecycle. It is optimized for cloud-native applications running in containers and Kubernetes. Using proven Dynatrace technologies, Dynatrace Application Security helps your DevSecOps teams resolve security issues faster, allowing them to accelerate software delivery. Its core capabilities are the following:
Runtime vulnerability analytics. Reduce the time and cost to find and fix application vulnerabilities. Use runtime context to precisely implement countermeasures and remediation.
Runtime application protection. Reduce exposure to missed and zero-day vulnerabilities. Continuously detect and block common application attacks, such as SQL injection and command injection.
Microsoft Sentinel is a security information and event management (SIEM) solution that enables customers to ingest data, monitor, alert, hunt, investigate, respond, and connect with different products, platforms, and services.
Natively integrating Dynatrace with Sentinel enables DevSecOps teams to rapidly detect, prioritize, triage, and remediate attacks. DevSecOps teams benefit from the high-accuracy threat signals Dynatrace surfaces. It helps them avoid time-consuming investigation activities, freeing them up for more important tasks.
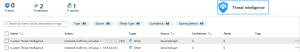
Sentinel data connectors poll Dynatrace for new attacks, vulnerabilities, audit logs and problem events, allowing Sentinel users to benefit from the solution’s comprehensive set of out-of-the-box Analytics Rule Templates and Playbook templates for building sophisticated detection and response capabilities.
- Sentinel Data connectors:
- Attacks. Common attacks on application layer vulnerabilities which can be detected and blocked using Dynatrace, like SQL injection, command injection, and JNDI attacks.
- Runtime vulnerabilities. Software vulnerabilities detected throughout all layers of the application stack.
- Audit logs. Security-relevant events for a Dynatrace tenant.
- Problems. AI-powered observability problems raised across cloud and hybrid environments.
- Sentinel Analytics Rules:
- Create incident (high severity) on attack detection
- Create alert (medium severity) on code-Level runtime vulnerability detection
- Create alert (medium severity) on third-Party runtime vulnerability detection
- Create alert (informational severity) on non-critical runtime vulnerability detection
In the following, we outline the Sentinel Playbooks:
- Add Dynatrace Application Security Attack Source IP Address to threat intelligence. Microsoft Sentinel provides a set of built-in rules which are able to use your added threat indicators. These rules are based on the type of threat indicator (domain, email, file hash, IP address, or URL) and the data source events you want to match. By automating the creation of threat indicators, it allows Sentinel to detect threats and automatically trigger remediation, for example, by blocking the IP address across all public endpoints. At the same time, DevSecOps teams are also alerted to ensure that vulnerabilities are correctly mitigated.
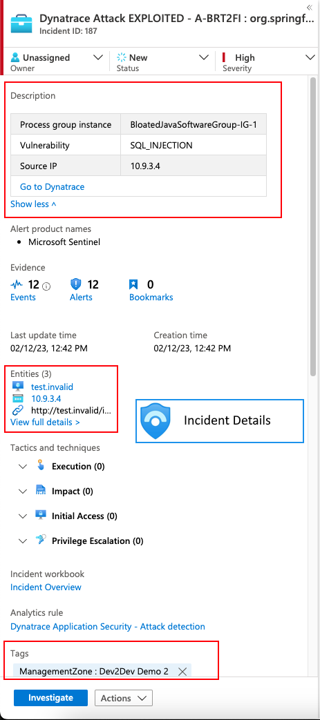
- Enrich Dynatrace Application Security Attack Incident. In addition to any automated remediation which is triggered by Dynatrace and/or Sentinel, DevSecOps teams still need to ensure that a vulnerability is fully mitigated. To support this activity, we can trigger automatic enrichment of Sentinel incidents which were reported by Dynatrace. This additional context allows DevSecOps analysts to quickly triage incidents using vulnerability type, source IP, exploited URLs, management zone, and tags.
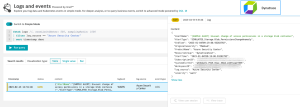
- Enrich Dynatrace Runtime Application Protection with related Microsoft Defender 365 Alerts. Customers using Runtime Application Protection are able to correlate security-relevant events across the Microsoft Defender 365 suite of products within Dynatrace. By providing this additional context within Dynatrace, DevSecOps engineers who are managing Attacks in the product are able to confirm whether an attempted exploitation of a vulnerability was successful or whether it was blocked. This integration provides unparalleled visibility for customers leveraging the Microsoft Defender 365 suite of products. Customers are also able to leverage the power of Grail™ to perform post-attack analytics to gain valuable insights into common attacker activities both before and after an exploit is triggered.

- Enrich Dynatrace Runtime Application Protection with related Microsoft Sentinel Security Alerts. Customers using Runtime Application Protection are able to correlate security-relevant events reported by all vendors which are connected to Microsoft Sentinel. By providing this additional context within Dynatrace, DevSecOps engineers who are managing Attacks in the product are able to confirm whether an attempted exploitation of a vulnerability was successful or whether it was blocked. This integration provides unparalleled visibility across a customer’s heterogeneous security vendor landscape. Customers are also able to leverage the power of Grail™ to perform post-attack analytics to gain valuable insights into common attacker activities both before and after an exploit is triggered.

- Ingest Microsoft Defender 365 alerts into Dynatrace. Customers relying on the Dynatrace software intelligence platform are able to use the power of Grail™ to get answers to security questions, in real time, at scale, and on budget. By bringing security-relevant events reported by the Microsoft Defender 365 suite of products into Dynatrace, teams are able to identify emerging attacks across their environment, using Dynatrace Notebooks for advanced, ad-hoc analytics and AutomationEngine to define complex remediation or alerting workflows.
- Ingest Microsoft Sentinel Security Alerts into Dynatrace. Customers relying on the Dynatrace software intelligence platform are able to use the power of Grail™ to get answers to security questions, in real time, at scale, and on budget. By bringing security-relevant events reported by all vendors which are connected to Microsoft Sentinel into Dynatrace, teams are able to identify emerging attacks across their heterogeneous security vendor landscape. Supported by Dynatrace Notebooks for advanced, ad-hoc analytics and AutomationEngine to define complex remediation or alerting workflows.




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum