In a complex data-driven world, many security vulnerabilities and attacks can jeopardize an organization’s sensitive data. Perhaps the most difficult, however, are zero-day attacks.
Malicious attackers have gotten increasingly adept at identifying vulnerabilities and launching attacks to exploit these weak points in IT systems.
A zero-day attack is a cyberattack in which an organization or developer only learns of a flaw as it’s being exploited in that organization’s IT systems—which means that IT teams have “zero days” to fix the flaw.
According to some data, a surge in verified zero-day exploits in 2021 alone accounted for 40% of zero-day attacks undertaken in the past decade.
Zero-day attacks are a key theme at Black Hat 2022, a security conference taking place August 6-11 in Las Vegas. The centrality of zero-day attacks suggests that organizations need a better strategy to fend off these attacks. But they also need a better strategy to address these attacks if they have IT systems and live applications that are already compromised.
Cyberattacks such as the Log4Shell vulnerability, which emerged in late 2021, demonstrated the importance of having a runtime application vulnerability strategy. Advanced observability tools can enable organizations to identify and address dangerous zero-day vulnerabilities, such as Log4Shell. Such tools can prevent bad actors from injecting malicious code into applications that are accessible to the outside world. Further, by automating DevSecOps release validation through quality gates, organizations can ensure their releases are secure by default.
In this guide, we explore runtime application security strategies and how observability and application security can converge to protect organizations from the threats zero-day attacks pose.
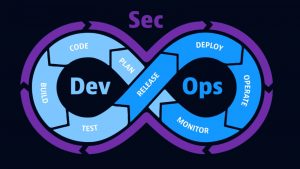
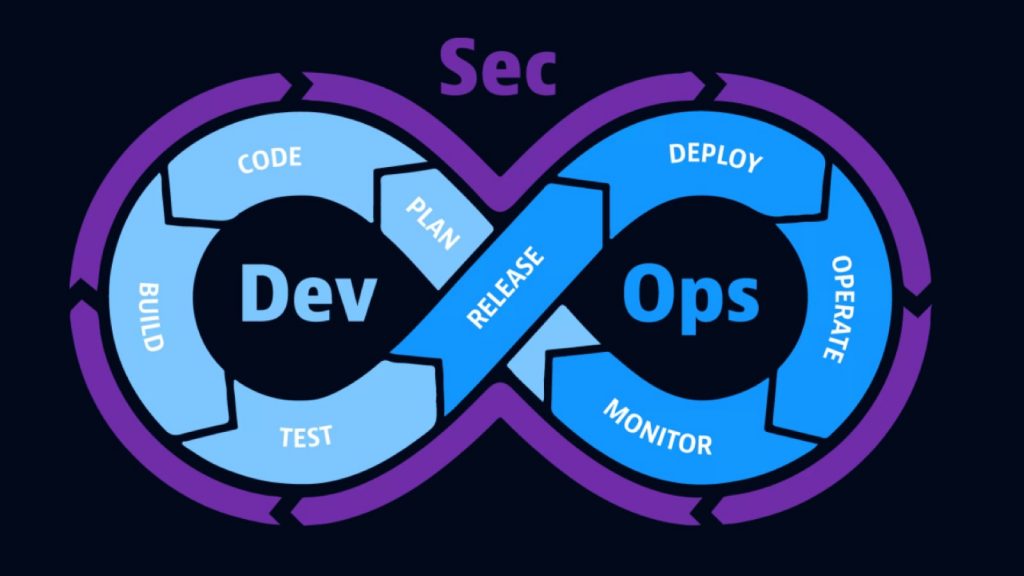
DevSecOps: Integrating security into DevOps
Traditional approaches to application security struggle to keep up with the complexity presented by cloud-native environments and rapid software release cycles. As organizations hasten software development cycles to remain competitive, security vulnerabilities can make their way into live applications, because developers simply don’t have time to find and fix them. To address this, organizations are integrating DevOps and security, or “DevSecOps,” to detect and respond to software flaws in production faster and with more efficiency.
DevSecOps ensures that teams can address security concerns early in the software development lifecycle as well as in production. This approach helps organizations strengthen their application security, so they can better protect users and the business from cyberattacks, including zero-day attacks and data breaches.
Learn more about securing modern applications and infrastructure, and how to integrate security into your DevSecOps initiative with the following resources:
 |
What is DevSecOps? – blog
DevSecOps connects three different disciplines: development, security, and operations. Learn how security improves DevOps. |
 |
Security as code demands proactive DevSecOps – blog
Learn what “security as code” is, how to build a “security as code” culture, and why organizations must adopt a proactive DevSecOps stance. |
 |
DevSecOps automation improves application security in multicloud environments – blog
DevSecOps automation is essential for ensuring application security in multicloud environments. Learn how to automate DevSecOps at scale. |
 |
DevOps vs. DevSecOps – blog
Consider how to incorporate security practices into your software delivery workflows, to protect your users and your business. Read more now. |
 |
Automated DevSecOps release validation ensures security by default – blog
In modern cloud-native environments, which rely on microservices architectures, application teams that are responsible for innovation face some dilemmas. |
Runtime vulnerability management: Staying ahead of zero-day attacks
Flexibility and agility are two major reasons why organizations are increasingly adopting cloud-native and open source technologies. Hybrid and multicloud environments are crucial for organizations looking to scale; however, they breed complexity that many traditional security solutions cannot adequately manage.
Moreover, with increased agility, organizations are now releasing new code faster than ever before. To facilitate software development in these faster release cycles, teams are turning to open source code libraries. Though convenient, third-party libraries can contain vulnerabilities that have the potential to compromise applications and sensitive data. Consider, for example, the recent Log4Shell and Spring4Shell vulnerabilities, which led to zero-day attacks.
A traditional, layered security posture is no longer enough. According to recent data, identifying and patching a vulnerability can take almost 7 months. How can organizations stay ahead of runtime vulnerabilities before they threaten sensitive information?
 |
What is Log4Shell? The Log4j vulnerability explained (and what to do about it) – blog
The Log4j vulnerabilities have triggered millions of exploit attempts of the Log4j 2 library. Learn all you need to know about Log4Shell. |
 |
How Dynatrace uses Dynatrace to combat the Log4j vulnerability (Log4Shell) – blog
As a result of the Log4j vulnerability, the Dynatrace security team explains how they use the Dynatrace platform to stay ahead of the impact. |
 |
Identify and minimize production risk of Log4Shell – blog
For many organizations around the world, time is of the essence to mitigate the vulnerability in the Apache log4j 2 library. Learn the top three criteria to prioritize. |
 |
Log4Shell highlights the need for secure digital transformation – blog
Modern observability and vulnerability management gave Avisi the secure digital transformation strategy they needed to conquer Log4Shell. |
 |
Spring4Shell: Detect and mitigate new zero-day vulnerabilities in the Java Spring Framework – blog
Spring4Shell vulnerabilities expose Java Spring Framework apps to exploitation. Learn how to prevent its effects—and those of similar vulnerabilities. |
Zero-day attacks: Facing the unexpected head on
With organizations adopting remote work policies and investing in their online presence, cyber attackers are taking advantage of the recent shift towards digital, wreaking havoc on organizations, sensitive data, and software supply chains.
By definition, zero-day attacks take organizations by surprise. “Zero day” means bad actors discover and exploit security vulnerabilities before experts learn about them. As a result, teams have “0 days” to remediate such issues and are always at risk. While IT teams can be diligent at identifying vulnerabilities, these weaknesses are difficult to detect. Also, attackers can almost always find a loophole using strategies like phishing scams, watering hole attacks, business email compromise attacks, malicious sites, unauthorized access, and more.
Check out these resources to learn more about these attacks and how you can protect your organization:
 |
Protect your organization against zero-day vulnerabilities– blog
Zero-day vulnerabilities put organizations’ data at risk. Learn how to ward off these vulnerabilities to protect your data from zero-day attacks. |
 |
Why software supply chain attacks are increasing – blog
Myriad software supply chain attacks continue to plague the global flow of goods. Here’s how modern observability takes aim at cybersecurity risks. |
 |
3 DevSecOps practices to minimize the impact of the next Log4Shell – article
Important lessons from Log4Shell – a critical vulnerability that left much of the IT world vulnerable to zero-day attacks. |
 |
Log4Shell vulnerability discovery and mitigation require automatic and intelligent observability – blog
Log4Shell made apps and devices worldwide susceptible to attack. Vulnerability monitoring in production must be a priority these days. |
 |
Dynatrace Application Security automatically detects and blocks attacks in real time – blog
Dynatrace has enhanced its Application Security Module to provide real-time, automatic attack detection and blocking. Learn more! |
 |
Runtime vulnerability management is still a vexing challenge for organizations – blog
Organizations are releasing code faster to keep up with today’s competitive landscape. But rapid code cycles also introduce runtime vulnerability management threats. |
To learn more about the risks of zero-day vulnerabilities and how to build runtime application security strategies to mitigate them, see the report Observability and security are key to closing vulnerability gaps.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum