A new high-severity remote code execution (RCE) vulnerability was disclosed on October 13, 2022. The vulnerability affects the Apache Commons Text library. While some view CVE-2022-42889, aka Text4Shell, as the following Log4Shell vulnerability, others see its impact as less severe.
A remote code execution vulnerability is a cyberattack in which an attacker can remotely execute commands on a user’s computing device.
CVE-2022-42889 is not as critical as Log4Shell
Since this is a remote code execution vulnerability in an open source Java library, it has been compared with Log4Shell. This vulnerability emerged in December 2021 and affected millions of production applications.
But current analysis indicates that the Apache Commons Text vulnerability is not as widespread and much harder to exploit. Although the NVD severity rating is reported as 9.8, the vulnerability is undergoing reanalysis. Other agencies rate the vulnerability as less severe because the library is not as ubiquitous and the vulnerability is harder to exploit than other similar vulnerabilities. In either case, organizations should upgrade to the latest library version (1.10.0), which addresses the issue.
The Commons Text library provides tools for processing text, including functionality to escape and unescape text. It computes the similarity and distance between strings and substitutes variables within a string. The string interpolation makes it possible to dynamically evaluate and expand properties by using a prefix to locate an instance of org.apache.commons.text.lookup.StringLookup.
Starting with version 1.5, the standard lookups include interpolators that could make this vulnerability exploitable:
- “script” to execute expressions using the JVM (or Java Virtual Machine) script execution engine (javax.script)
- “dns” to resolve DNS records
- “url” to load values from remote servers via URLs
The vulnerability affects versions 1.5 to 1.9 of the library and has already been patched in Apache Common Text version 1.10.0.
How to determine whether your organization is affected
To determine whether your organization is affected by the Apache Common Text vulnerability, you need to evaluate whether one of the vulnerable versions of the library is being used in your applications. A simple approach could be to look for the individual jar files:
- commons-text-1.5.jar
- commons-text-1.6.jar
- commons-text-1.7.jar
- commons-text-1.8.jar
- commons-text-1.9.jar
But this might not be easy to accomplish in a large environment, especially in cloud deployments.
Detecting the Apache Commons Text vulnerability using Dynatrace Application Security
Dynatrace Application Security will detect the vulnerability automatically and identify whether your organization is affected. If so, it will be listed under the third-party vulnerabilities section. You can use the filters to quickly identify it by selecting Snyk/CVE ID in the Filter By field and search for “CVE-2202-42889,” as shown in the following screenshot.
If you have configured security notifications, IT teams can receive a notification as soon as the vulnerability is discovered.
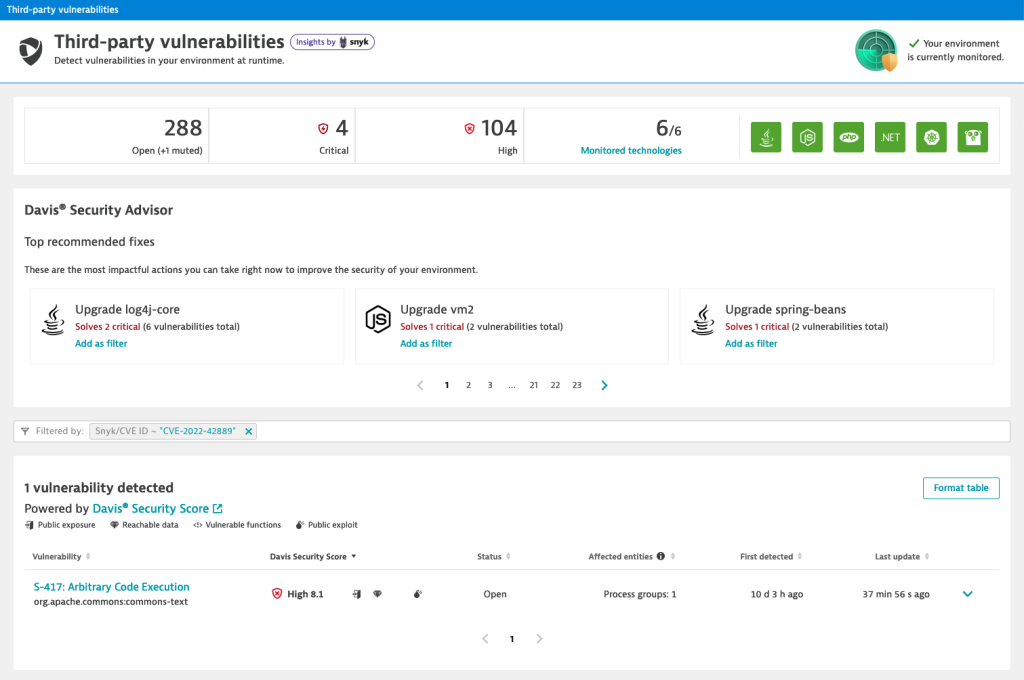
Detecting the Apache Commons Text vulnerability using the Maven dependency tree
To quickly identify if projects are affected, you can use the Apache Maven dependency plugin to see if one of the vulnerable versions is in your project.
mvn dependency:tree -Dincludes=org.apache.commons:commons-text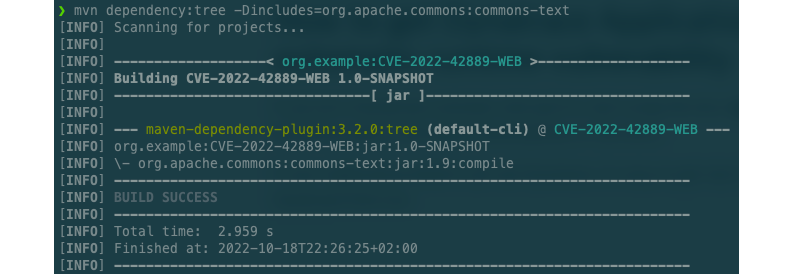
The Apache Software Foundation resolved the vulnerability in Apache Commons Text 1.10.0, and organizations should upgrade to that version as soon as possible.
How to get Dynatrace Application Security for automatic runtime vulnerability analysis
If you are a Dynatrace customer and want to start using the new Application Security module, go to the Dynatrace web UI and select Vulnerabilities in the menu.
If your organization doesn’t yet use Dynatrace, it’s easy to get started in less than five minutes with the Dynatrace free trial.




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum