Dynatrace adds Go vulnerability analysis on top of Java, .NET, Node.js, and PHP vulnerability analysis. Coverage extends to language runtimes such as Java Virtual Machine (JVM), Node.js runtime, and .NET CLR. This helps SecOps, DevOps, and operations teams to collaborate more effectively. Automatic vulnerability detection at runtime and AI-powered risk assessment further enable DevSecOps automation.
In addition to modern application stacks introducing new levels of speed and complexity, they also create new security challenges. And the distinction between applications and cloud platforms is blurring.
Missing holistic vulnerability analysis creates risk
Every layer of an application stack contributes to the security posture of an application and can potentially contain vulnerabilities. The number of entry points through which attackers can infiltrate your company’s environment is always expanding. SecOps teams are confronting increasingly complex threats and alert storms. And while effective DevSecOps approaches require collaboration and automation, teams still often work alone in silos.
This is because many organizations lack a holistic view and analysis across all layers of their application ecosystem to minimize the attack surface and protect the weakest links. DevOps teams, SREs (site reliability engineers), platform teams, and SecOps teams aren’t always working from a common source of truth:
- SAST tools (static application security testing) provide scanning code for vulnerabilities.
- Vulnerability scanners detect vulnerabilities in, for example, language runtimes.
This siloed approach renders holistic risk assessment impossible and can lead to ineffective issue prioritization and blind spots.
Dynatrace uniquely provides full-stack Runtime Vulnerability Analysis
With new enhancements, Dynatrace Application Security now provides Runtime Vulnerability Analysis across the entire application stack in cloud-native environments. Uniquely, Dynatrace not only identifies vulnerabilities across all layers, it also analyzes them automatically. This provides actionable out-of-the-box insights to CISOs and SecOps teams that can be used to assess risk, prioritize, and collaboratively remediate threats with other teams.
With the flip of a switch and zero configuration, Dynatrace gives you:
- AI-powered risk assessment based on observability data provided by the Davis® Security Advisor
- DevSecOps collaboration for faster remediation across all layers
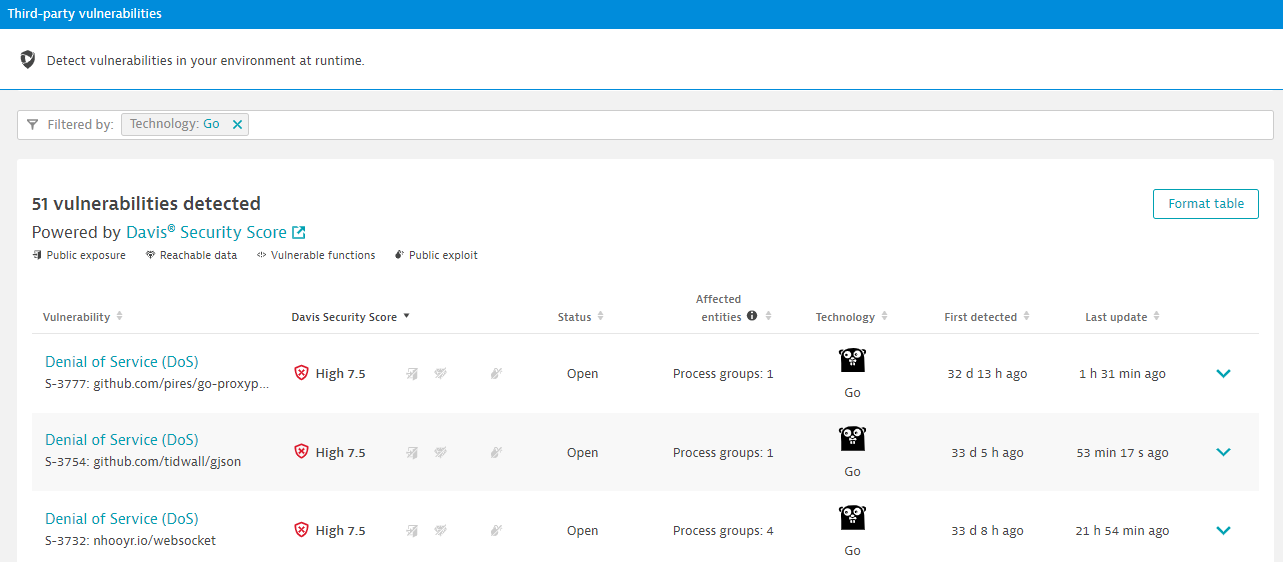
Dynatrace adds AI-powered vulnerability analysis for Go
Dynatrace extends its Runtime Vulnerability Analysis to Go on top of Java, .NET, Node.js and PHP. Go is one of the key technologies powering cloud-native applications and its adoption is increasing rapidly. Even Kubernetes and its core services—a key driver in modern cloud transformation—are written in Go.
Runtime Vulnerability Analysis is provided across the entire software development lifecycle, from pre-production to production for every operating environment, including dynamic multiclouds and Kubernetes clusters. The Dynatrace Davis AI engine aggregates vulnerability data in real time and recommends actions to improve the security of your Go applications.
Vulnerability Analysis for language runtimes completes the picture
Runtimes like Java Virtual Machine (JVM) and .NET CLR, or Node.js runtimes are responsible for converting bytecode into machine-specific code. Insights into this layer and the respective vulnerabilities are crucial, especially in containerized environments where every container has its own runtime.
Dynatrace customers get full visibility into language runtime vulnerabilities. This helps accelerate remediation by leveraging observability data to automatically provide an inventory of all deployed versions.
Automatic vulnerability analysis for Kubernetes platform versions
In cloud-native application stacks, everything is code. Just securing applications and libraries isn’t enough. You need to go deeper into the stack—into the infrastructure itself. This is why Dynatrace announced automatic vulnerability detection to the Kubernetes platform last year. As for the other components, Dynatrace Application Security detects vulnerable Kubernetes versions automatically and tracks the evolution of these security problems in real time.
How to get started
Runtime Vulnerability Analysis for Go and language runtimes will be available within the next 90 days.
If you’re already a Dynatrace customer and want to start using the Application Security module today, just select Application Security from the menu in the Dynatrace web UI.
If you’re not using Dynatrace yet, it’s easy to get started in under 5 minutes with the Dynatrace free trial.
For more information, visit our website to watch the demo or read our previous Application Security blog posts. To learn more, see Application Security in Dynatrace Documentation.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum