With Dynatrace Synthetic Monitoring, you can easily monitor the availability and performance of your applications as experienced by your customers around the world and around the clock. Your applications usually require authentication and authorization (user ID, password, token, or certificate) as part of the business-critical path you wish to monitor (using private or public monitors).
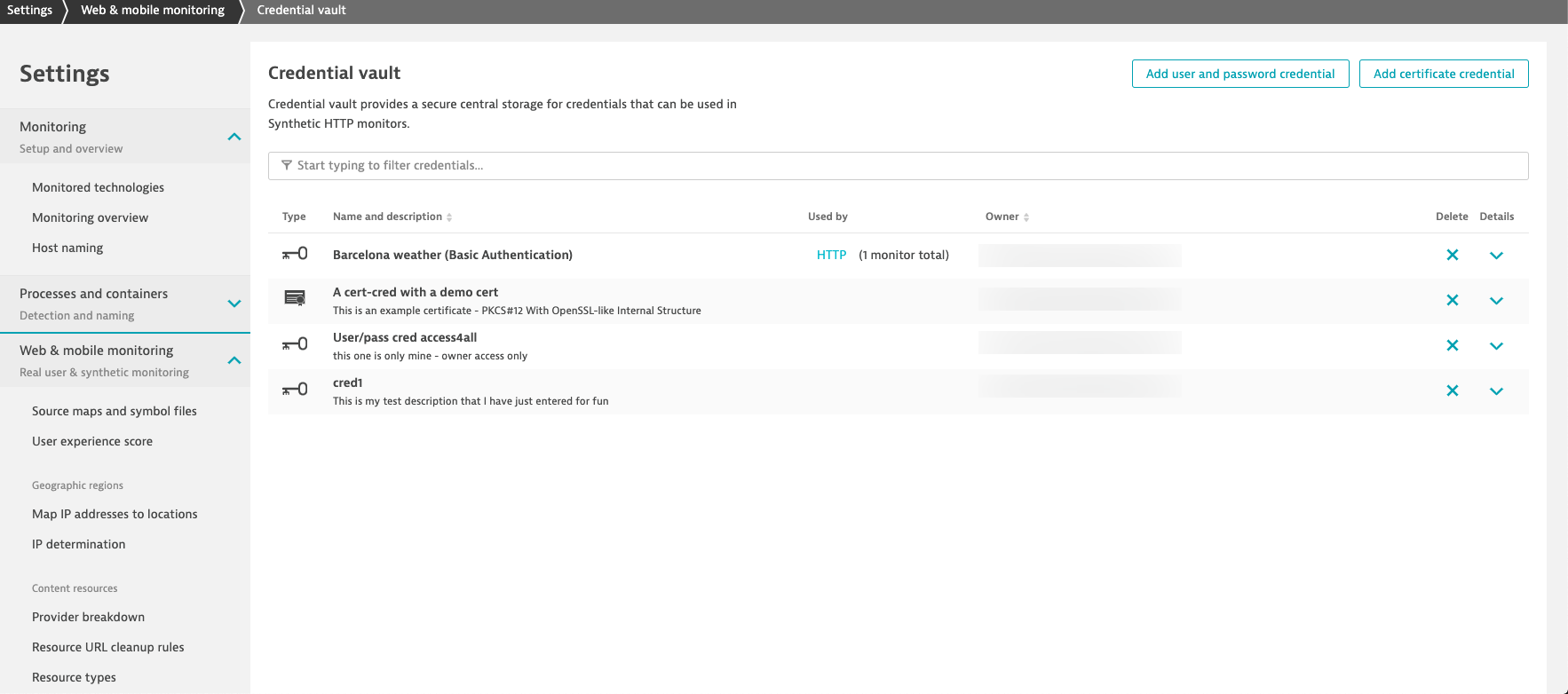
To provide you with a secure way to store your credentials and an easy way to handle them, we’ve implemented a credential vault—a central place in Dynatrace to store all your sensitive information that is to be used with Dynatrace Synthetic.
Safely store your credentials in a central place, automatically update monitors, and more!
First and foremost, the Dynatrace Synthetic credential vault provides a secure store for your credentials.
The sensitive information in each credential, be it a user ID/password or certificate, is stored in Advanced Encryption Standard (AES) encrypted form in the database on the Dynatrace Cluster. Access to the data is granted only through a secure SSL channel. This means that after credentials are added to the credential vault, they won’t be visible to you or any other user in your organization; they are visible only to the synthetic monitors referencing them. The description and metadata of a credential can be displayed, but the sensitive information is available only for overwriting.
Automatically update monitors by accessing the credential vault via REST API
You can access the credential vault by API, which lets you integrate it with external credential storage systems. This lends itself to a vast range of automation use cases. For example, it lets you automatically update monitors depending on information pulled by a specific monitor. Simply making a PUT REST API call to a given credential allows you to update that credential. As credentials are used by synthetic monitors as a reference, such an update will immediately impact all the other monitors referencing the credential.
Easily rotate passwords
It might be the case that you run many synthetic monitors and your policies require regular password changes. If so, a centralized place to store credentials makes it easier for you to rotate passwords.
Make sure your credentials can’t be reused by other users
Now you can create credentials that are accessible only by you, the owner. Monitors that use such credentials can’t be reused (duplicated/edited) by other users in a way that would require referencing credentials that they don’t have access to. To save such a monitor after editing, other users have to provide credentials that they have access to.
How to use the credential vault for Dynatrace Synthetic
Note: The credential vault is currently available for HTTP monitors, with browser monitors to follow soon.
You might have already noticed that while creating or editing your synthetic HTTP monitors, those credentials are already stored in the credential vault, whether you use basic authentication or certificate-based authentication.
- Basic authentication
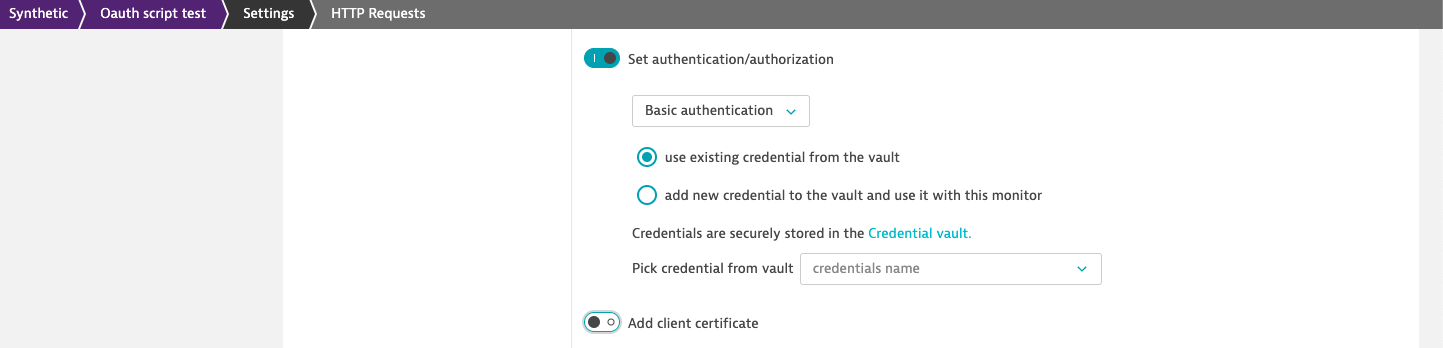
Authentication/authorization already uses the credential vault to store sensitive information - Certificate-based authentication
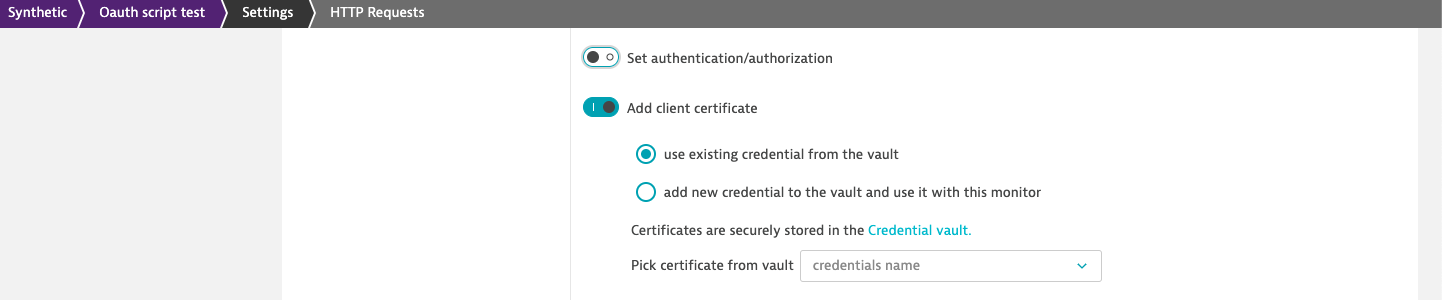
Certificates your monitors use for authentication are also stored in the credential vault
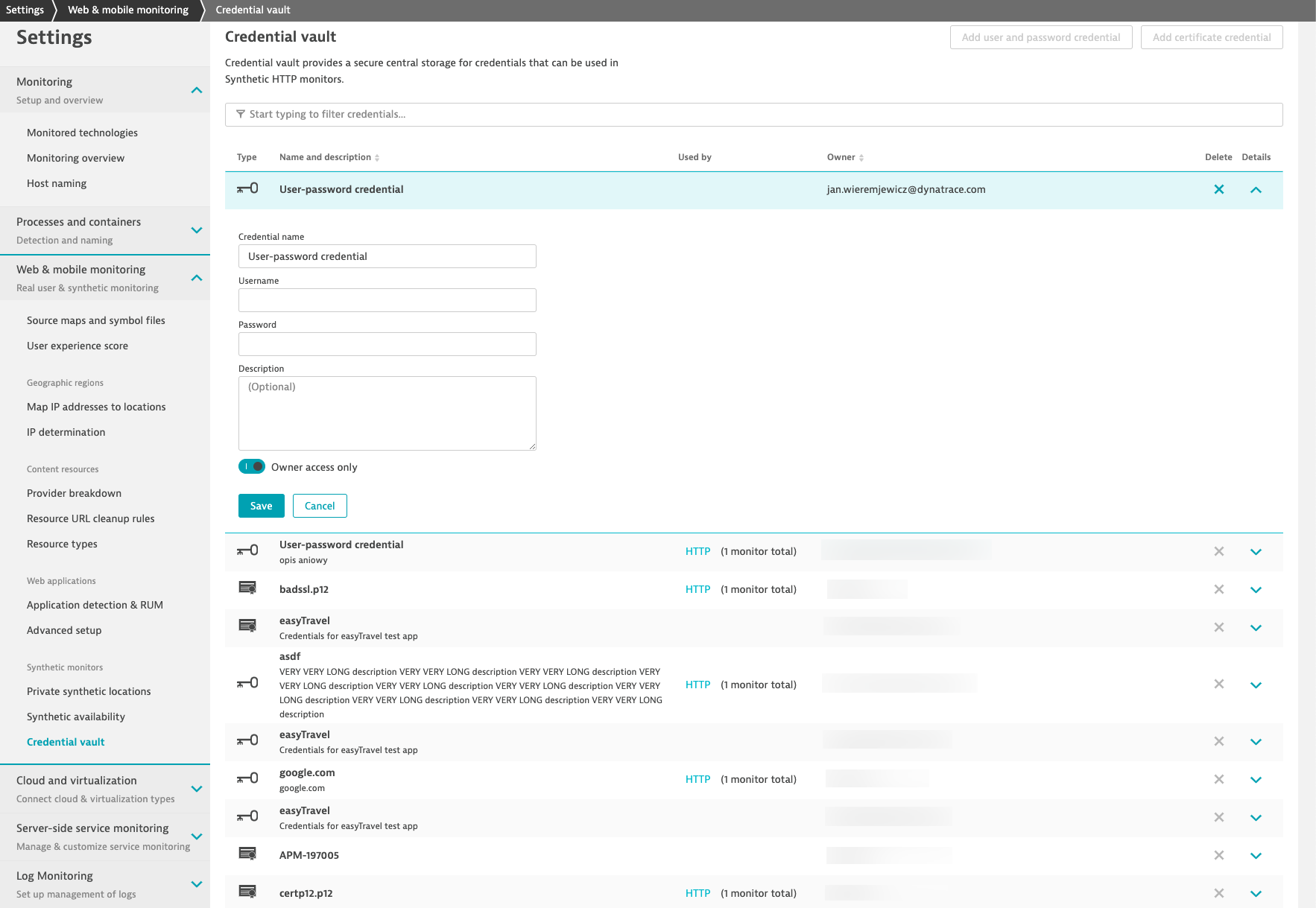
You can add new credentials to the credential vault. Please note that, currently, you can limit access to a credential to:
- Everyone
- Owner only
So if a monitor uses a credential that is accessible only by the owner, there are restrictions as to who can change the monitor while using a given credential. We always recommend using dedicated test credentials for synthetic uses. This ensures that the credential added to a monitor is used only in the manner that the owner wishes.
For security reasons, once entered in the credential vault, credentials can’t be displayed. That means that after you’ve entered a user ID/password set, you’ll need to overwrite it rather than display it. This hard security requirement is in effect in both the UI (in visual as well as script mode) and the API.
Is anything going to change for me?
With enhanced security come changes:
- Existing monitors have automatically been migrated to the credential vault. This means that if you have been using authentication/authorization in your HTTP monitors, these are now moved to the credential vault. Feel free to review the availability of these and the access rights for them.
- If a credential is set as Owner access only and added to a monitor, that means that only the owner can:
- Edit the monitor and save it using that credential (others will have to replace such a credential with one that they can access to successfully save changes)
- Duplicate/copy the monitor and save it with that credential.
- As the credentials are no longer stored in the monitor script, they are not visible when editing the script. What’s now visible is the credential-vault identifier related to the credential stored in the vault.
- As in the UI, when using the API, the credentials for a given monitor won’t be visible either from the Credential vault API or the Synthetic API endpoints.
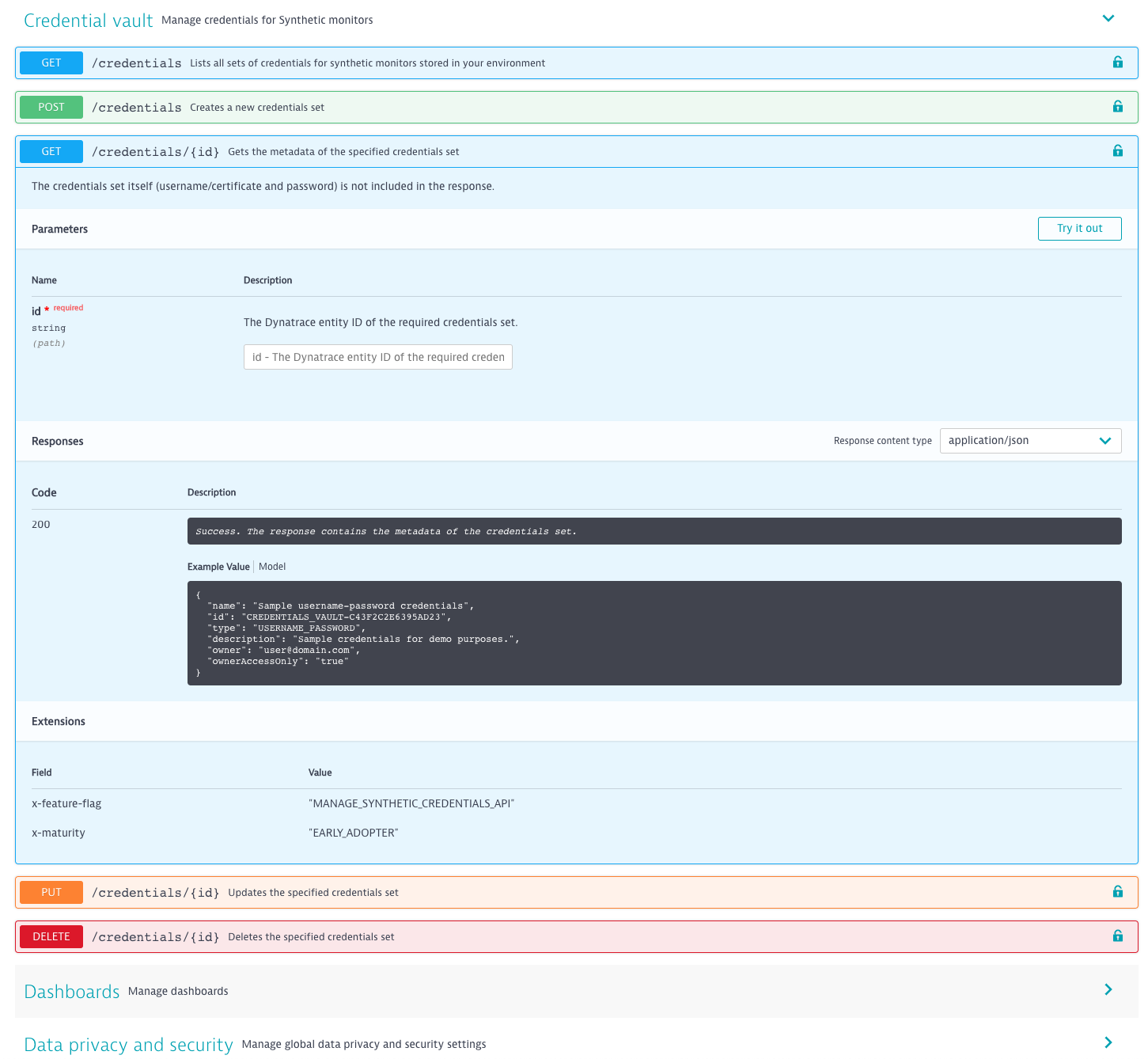
Start using the credential vault for synthetic HTTP monitors
Existing monitors have automatically been migrated to the credential vault, so chances are that you’re already using the credential vault for your synthetic HTTP monitors.
To access the credential vault and see what credentials are already available to you starting with Dynatrace version 1.183, check Settings > Web & mobile monitoring > Credential vault.
What’s next?
We’re planning some enhancements for the credential vault:
- Enabling browser monitor usage of credentials stored in the credential vault
- A new credential type, token—a generic credential type with only one secure value, which can be a token, secret, or some passphrase
- The ability to use stored credentials in HTTP monitors for purposes other than authentication/authorization and certificate forms
Besides that, keep a watch for new Synthetic Monitoring public locations coming soon!




Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum