

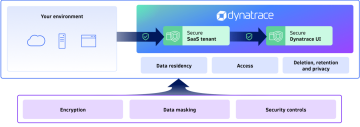
Dynatrace protects data end-to-end
-
Data encryption at rest
Data at rest is encrypted and separated from the data of other customers.
-
Data masking
Sensitive data is masked to ensure it never leaves your environment, isn’t stored, or won’t be shown to unauthorized users.
-
Security controls
Dynatrace components are secure by design and default through a multi-layered security development lifecycle (SDLC).

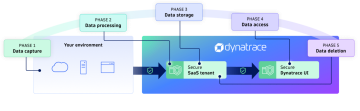
You control data through its lifecycle
Security and privacy controls described earlier are applied in different steps of the data lifecycle to give you flexibility in configuring Dynatrace to control how the data is protected across its whole lifecycle.
- Phase 1
Data capture
Control which data does not leave your environment and is not ingested into the Dynatrace platform.
- Phase 2
Data processing
Control which data from the data sent to Dynatrace will be anonymized before storing.
- Phase 3
Data storage
Control how long data will be stored in Dynatrace and define custom retention periods for each Grail bucket.
- Phase 4
Data access
Control permissions to access and view the data both on API and UI levels.
- Phase 5
Data deletion
In addition to the retention periods, support other use cases including hard-deleting individual records.
Trust center blogs
 BlogTailored access management, Part 2: Onboard users to Grail and AppEngine
BlogTailored access management, Part 2: Onboard users to Grail and AppEngine BlogDynatrace SaaS achieves “Protected” status after successful completion of Australian Information Security Registered Assessors Program assessment (IRAP)
BlogDynatrace SaaS achieves “Protected” status after successful completion of Australian Information Security Registered Assessors Program assessment (IRAP) BlogPrivacy spotlight: Ensure compliance by hard deleting individual records in Grail
BlogPrivacy spotlight: Ensure compliance by hard deleting individual records in Grail