Ever wished you could take back something you said? It's simply not possible. The same holds true for passwords or tokens that are inadvertently exposed (for example, in public GitHub repositories). However, if you detect such exposures automatically and react quickly, you can greatly reduce their impact.
Especially in enterprise-wide environments, it’s challenging to centrally ensure that credentials are never exposed to unauthorized people. Credentials may, for example, be unintentionally exposed in log files, shared documents, and internal (or even external) source code repositories. Last year GitHub reported that they have identified one billion potential tokens committed to GitHub repositories in the first year of running their secret scanning service. Publicly exposed tokens present a particularly high risk because attackers can automatically find and abuse such tokens within minutes.
From the beginning, Dynatrace was developed with the highest level of security in mind. We’re constantly enhancing Dynatrace security features. An automated detection or prevention mechanism is the only reliable and scalable way of ensuring the highest possible security. A prerequisite for using such an automated approach is a token format that is precisely identifiable and doesn’t lead to false positives.
Therefore, we’re happy to introduce a new Dynatrace token format that will help you automate the protection of tokens within your organization.
Unique Dynatrace token format allows for automated prevention
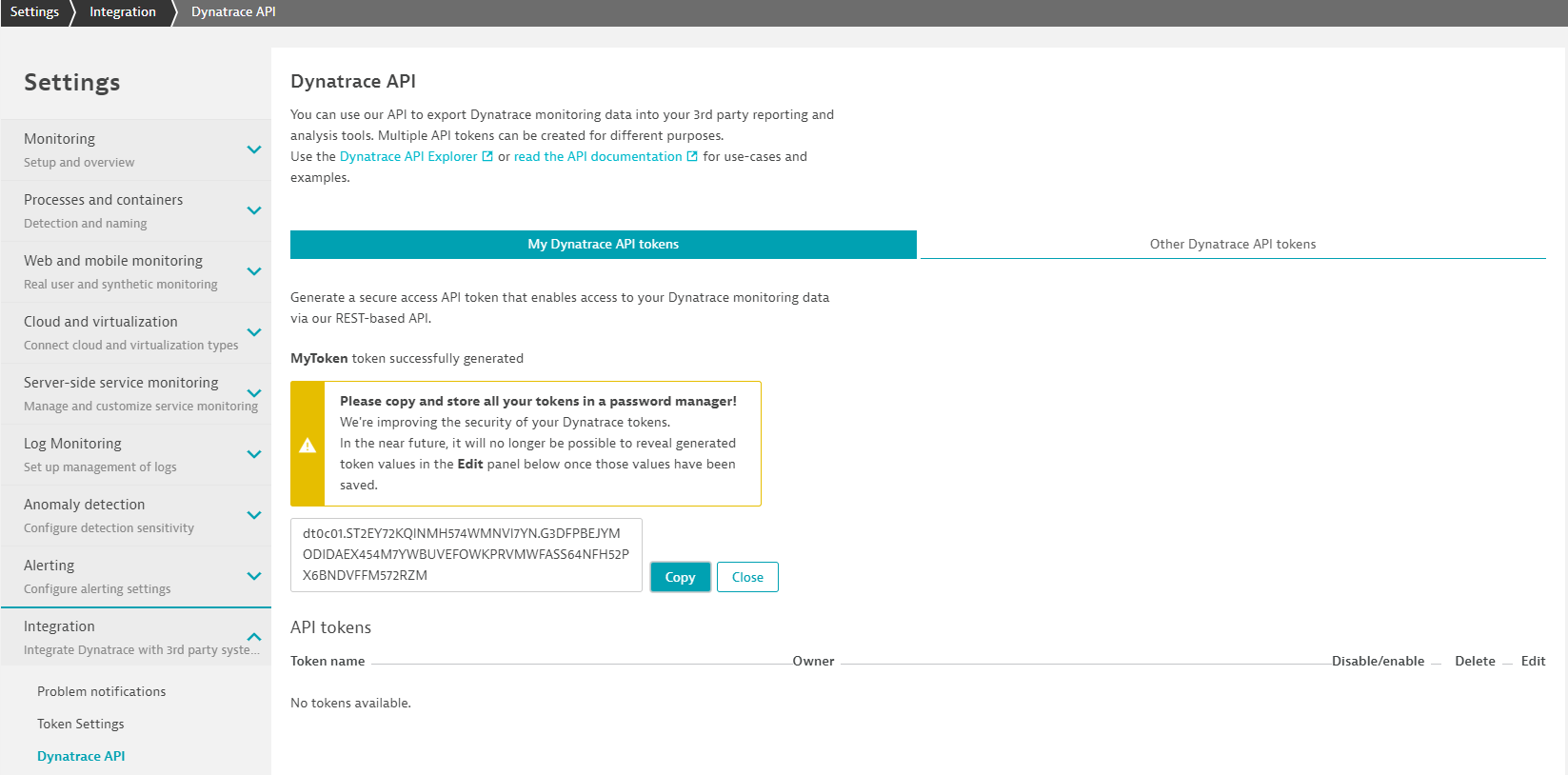
To allow for automated prevention mechanisms, Dynatrace is introducing a new and unique token format for our API tokens (see example below):
dt0c01.ST2EY72KQINMH574WMNVI7YN.G3DFPBEJYMODIDAEX454M7YWBUVEFOWKPRVMWFASS64NFH52PX6BNDVFFM572RZMThe tokens consist of three components separated by a dot.
dt0c01 |
Unique prefix identifying a Dynatrace API token |
ST2...7YN |
Public portion of token This is a 24-character public identifier of the token. This value can be safely displayed in the UI and can be used for logging purposes. |
G3D...RZM |
Secret portion of token This is a 64-character secret portion of the token, which can be treated like a password and therefore doesn’t need to be displayed in the Dynatrace web UI (following initial creation) or stored in log files. |
The new token format allows you to precisely match Dynatrace tokens using, for example, a regular expression:
dt0[a-zA-Z]{1}[0-9]{2}\.[A-Z0-9]{24}\.[A-Z0-9]{64}
How the new token format boosts security
The new token format provides several benefits:
Secure your internal use of tokens
Using pattern matching to find internal tokens gives you options for running automated security controls within your organization, such as (but not limited to):
- Using Git pre-commit hooks to avoid pushing tokens to source code repositories (for example, using tools like git-secrets)
- Defining masking rules to obfuscate the secret portions of tokens when writing log files
- Detecting tokens in internal files or communications
GitHub secret scanning service
Adopting the new token format will enable the GitHub secret scanning service to identify any token pushed to a public GitHub repository that matches the new Dynatrace API token format. Dynatrace has already begun working with GitHub to receive such information; we’re currently looking into ways to automatically alert you in cases where an exposed Dynatrace token is detected by GitHub.
Smooth adoption of the new format
The change over to the new token format will be rolled out in two steps, giving you full control over their adoption.
Step 1: Option to configure new tokens using the new format
You can opt-in to the new token format to verify and ensure that your automation can handle the format change without any problems (this setting is turned Off by default). When you turn on the new token configuration setting, all new API tokens will be generated using the new format (existing tokens will continue to work).
- This setting is available with Dynatrace version 1.205 (Go to Settings > Integration > Token Settings).
- Dynatrace Managed deployments
- This setting is available for environment tokens with the release of Dynatrace Managed version 1.206 (in the Dynatrace web UI, go to Settings > Integration > Token Settings).
- This setting is available for cluster tokens with the release of Cluster Management Console 1.208 (in the CMC web UI, go to Settings > API tokens).
Step 2: Tokens will be configured to use the new token format by default
With the rollout of Dynatrace version 1.210, this setting will be turned on by default (i.e., all newly generated tokens will use the new format). You’ll still have the option to opt-out of the new token format for a limited period of time.
What you need to do
- Verify that your automation can handle the change in token format by using the configuration option in Dynatrace version 1.205.
- Rotate all your existing tokens so that your old tokens are exchanged with new tokens that use the new format.
Note: We recommend that you regularly rotate your API tokens using the Dynatrace Tokens API or the Cluster API (for Dynatrace Managed deployments).
What’s next
To further extend the automation around secure token handling, we plan to
- Ensure that all Dynatrace-issued tokens use the new token format (with different prefixes and varying token lengths depending on the use case (for example, see Dynatrace SCIM tokens)
- Enable automated detection of leaked tokens and an alerting mechanism
So please stay tuned for upcoming announcements!
As always, we look forward to hearing your feedback at Dynatrace answers or via Dynatrace ONE in-product chat.
Start a free trial!
Dynatrace is free to use for 15 days! The trial stops automatically, no credit card is required. Just enter your email address, choose your cloud location and install our agent.





Looking for answers?
Start a new discussion or ask for help in our Q&A forum.
Go to forum